The Google Capture The Flag (CTF) was run on the 29th and 30th of April 2016, this is my solution to the forensics challenge “For1” which was worth 100 points.
In this challenge a 200mb dump1.raw.lzma file was provided with no other instructions other than to find the flag. After downloading the file I decompress it to reveal a 900mb dump1.raw file.
root@kali:~# lzma -d dump1.raw.lzma root@kali:~# file dump1.raw dump1.raw: ELF 64-bit LSB core file x86-64, version 1 (SYSV)
Upon first look it appears to be an ELF file, however this is just the start of what appears to be a memory dump. After running binwalk against the dump I start to see a lot of “Microsoft portable executable” content. After running strings against the dump file I notice a lot of references to Microsoft/Windows confirming that this appears to be a memory dump from a Windows OS running within VirtualBox.
As this appears to be a memory dump I start using volatility, an open source memory forensics tool. Initially I’m not getting any results with volatility, after further searching through the dump I see references to Windows 10 and assume that my version of volatility does not have Windows 10 support. After checking the volatility website I confirm that I need version 2.5 which introduces Windows 10 support.
With the new version downloaded I ran “imageinfo” to determine the profile that volatility would recommend, but failed to get any useful information. At this point I simply guessed that it was Win10x64 which worked, so ran with this profile and performed a pslist to list all running processes at the time of the memory dump, output shown below.
root@kali:~/volatility-master# ./vol.py -f /root/dump1.raw pslist --profile=Win10x64 pstree Volatility Foundation Volatility Framework 2.5 Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0xffffe00032553780 System 4 0 126 0 ------ 0 2016-04-04 16:12:33 UTC+0000 0xffffe0003389c040 smss.exe 268 4 2 0 ------ 0 2016-04-04 16:12:33 UTC+0000 0xffffe0003381b080 csrss.exe 344 336 8 0 0 0 2016-04-04 16:12:33 UTC+0000 0xffffe000325ba080 wininit.exe 404 336 1 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000325c7080 csrss.exe 412 396 9 0 1 0 2016-04-04 16:12:34 UTC+0000 0xffffe00033ec6080 winlogon.exe 460 396 2 0 1 0 2016-04-04 16:12:34 UTC+0000 0xffffe00033efb440 services.exe 484 404 3 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe00033f08080 lsass.exe 492 404 6 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe00033ec5780 svchost.exe 580 484 16 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe00034202280 svchost.exe 612 484 9 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000341cb640 dwm.exe 712 460 8 0 1 0 2016-04-04 16:12:34 UTC+0000 0xffffe00034222780 svchost.exe 796 484 45 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000342a7780 VBoxService.ex 828 484 10 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000342ad780 svchost.exe 844 484 8 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000342c0080 svchost.exe 852 484 6 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000342dd780 svchost.exe 892 484 18 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000342bc780 svchost.exe 980 484 17 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe00034377780 svchost.exe 608 484 17 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000343e7780 spoolsv.exe 1072 484 8 0 0 0 2016-04-04 16:12:34 UTC+0000 0xffffe000343e9780 svchost.exe 1092 484 23 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe0003442a780 rundll32.exe 1148 796 1 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe00034494780 CompatTelRunne 1224 1148 9 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe00034495780 svchost.exe 1276 484 10 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe0003461d780 svchost.exe 1564 484 5 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe000345da780 wlms.exe 1616 484 2 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe00034623780 MsMpEng.exe 1628 484 24 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe000343b2340 cygrunsrv.exe 1832 484 4 0 0 0 2016-04-04 16:12:35 UTC+0000 0xffffe0003479b780 cygrunsrv.exe 1976 1832 0 -------- 0 0 2016-04-04 16:12:36 UTC+0000 2016-04-04 16:12:36 UTC+0000 0xffffe000347aa780 conhost.exe 2004 1976 2 0 0 0 2016-04-04 16:12:36 UTC+0000 0xffffe000347c1080 sshd.exe 2028 1976 3 0 0 0 2016-04-04 16:12:36 UTC+0000 0xffffe00033e00780 svchost.exe 1772 484 3 0 0 0 2016-04-04 16:12:37 UTC+0000 0xffffe00033f1f780 sihost.exe 92 796 10 0 1 0 2016-04-04 16:12:37 UTC+0000 0xffffe0003259b3c0 taskhostw.exe 1532 796 9 0 1 0 2016-04-04 16:12:37 UTC+0000 0xffffe000339d4340 NisSrv.exe 2272 484 6 0 0 0 2016-04-04 16:12:38 UTC+0000 0xffffe000336e8780 userinit.exe 2312 460 0 -------- 1 0 2016-04-04 16:12:38 UTC+0000 2016-04-04 16:13:04 UTC+0000 0xffffe000336e3780 explorer.exe 2336 2312 31 0 1 0 2016-04-04 16:12:38 UTC+0000 0xffffe0003374f780 RuntimeBroker. 2456 580 6 0 1 0 2016-04-04 16:12:38 UTC+0000 0xffffe00033a39080 SearchIndexer. 2664 484 13 0 0 0 2016-04-04 16:12:39 UTC+0000 0xffffe00033a79780 ShellExperienc 2952 580 41 0 1 0 2016-04-04 16:12:39 UTC+0000 0xffffe00033b57780 SearchUI.exe 3144 580 38 0 1 0 2016-04-04 16:12:40 UTC+0000 0xffffe00033e1d780 DismHost.exe 3636 1224 2 0 0 0 2016-04-04 16:12:47 UTC+0000 0xffffe000348e9780 svchost.exe 3992 484 6 0 0 0 2016-04-04 16:12:52 UTC+0000 0xffffe000348c6780 VBoxTray.exe 3324 2336 10 0 1 0 2016-04-04 16:12:55 UTC+0000 0xffffe00034b08780 OneDrive.exe 1692 2336 10 0 1 1 2016-04-04 16:12:55 UTC+0000 0xffffe00034b0f780 mspaint.exe 4092 2336 3 0 1 0 2016-04-04 16:13:21 UTC+0000 0xffffe00034ade080 svchost.exe 628 484 1 0 1 0 2016-04-04 16:14:43 UTC+0000 0xffffe0003472b080 notepad.exe 2012 2336 1 0 1 0 2016-04-04 16:14:49 UTC+0000 0xffffe000349e4780 WmiPrvSE.exe 3032 580 6 0 0 0 2016-04-04 16:16:37 UTC+0000 0xffffe000349285c0 taskhostw.exe 332 796 10 0 1 0 2016-04-04 16:17:40 UTC+0000
There are a small handful of processes that look interesting to me straight away, including notepad.exe, sshd.exe, and mspaint.exe.
I think text from notepad.exe would have been revealed while I was running strings on the dump file, so I leave that for now. I quickly check for open connections of sshd.exe which appears to by running under Cygwin but can’t see any established connections so leave that one for now. Finally I decide to dump the mspaint.exe process (PID 4092), as shown below.
root@kali:~/volatility-master# ./vol.py -f /root/dump1.raw --profile=Win10x64 memdump -p 4092 -D /root/ Volatility Foundation Volatility Framework 2.5 ************************************************************************ Writing mspaint.exe [ 4092] to 4092.dmp
After dumping the process I had a 1.8gb file, which seemed pretty strange to have come from a 900mb dump file. I’m not too sure why this is, and after discussing with the challenge creator afterwards they did not seem to know why this was the case either. If anyone has any insight to this I’d be interested to hear.
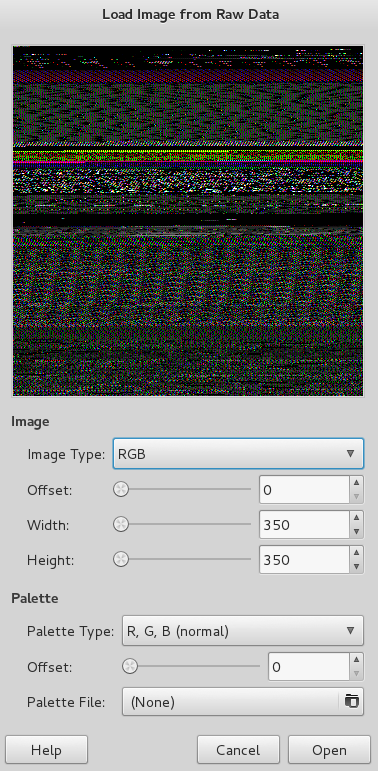
Regardless, at this point I did not yet know how to try and view any contents that were in paint from my process dump. After some quick research I found this post outlining how to extract images from memory. I simply renamed my exported 4092.dmp file to 4092.data so that it was recognized by Gimp, and then opened it in Gimp.
After opening the image, this is what I was given.
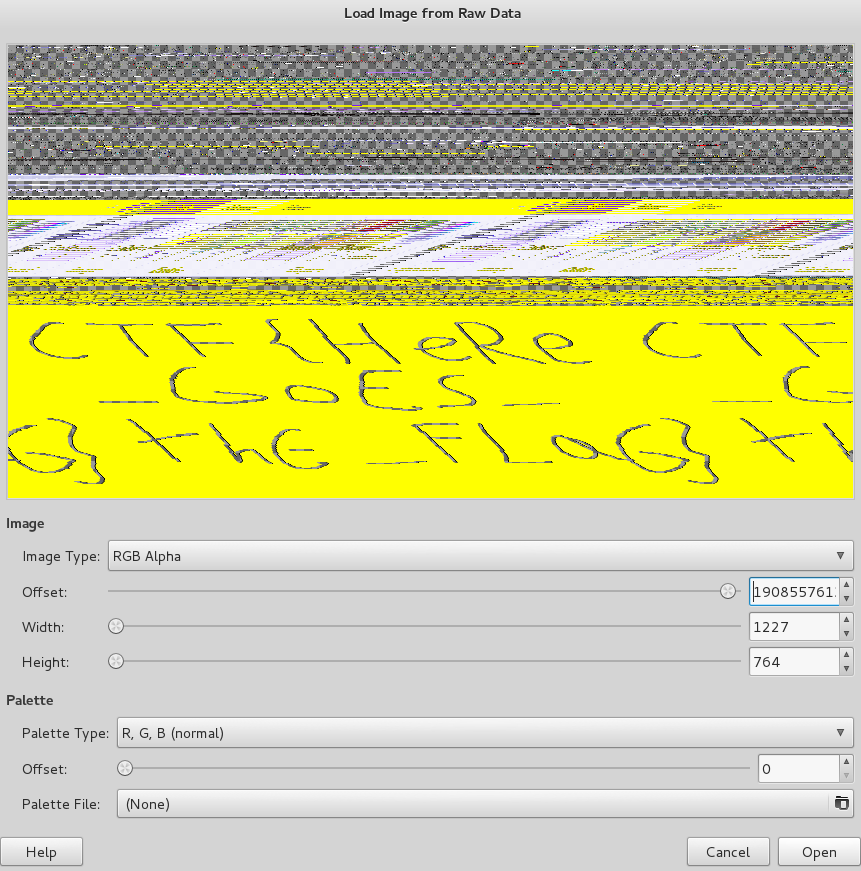
After holding the up arrow on the Offset field for a while, I decided that it would take a very long time to scrub through the 1.8gb file. I expanded the window and modified the width a bit to fit more in the screen and then started to drag the offset pointer around looking for anything interesting. Eventually with a lot of luck I found something, after adjusting the width further I found the flag shown below.
This resulted in the flag of CTF{HeRe_GoES_thE_FLaG}.
0 Comments.