We can implement AppLocker rules using Windows PowerShell in addition to group policy. AppLocker PowerShell cmdlets are used to make, test and troubleshoot AppLocker policy, however the cmdlets are designed to complement the AppLocker user interface that is configured through either local or group policy.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Implement AppLocker Rules Using Windows PowerShell
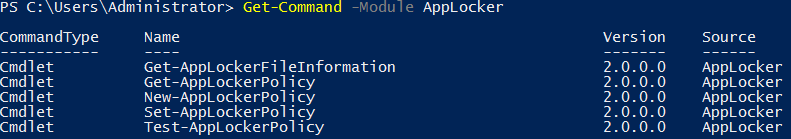
We can run the Get-Command PowerShell cmdlet and specify the AppLocker module to see all of the available cmdlets that implement AppLocker rules using Windows PowerShell.
As shown above there are currently 5 different PowerShell cmdlets available for interacting with AppLocker, we’ll explain each of these now.
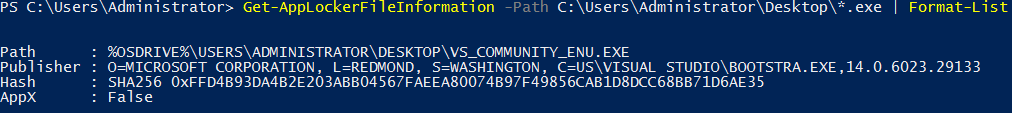
- Get-AppLockerFileInformation: This cmdlet gets the required information needed to create AppLocker rules from a list of files or the event log. In the example below, we can see the path, publisher, and hash for the .exe file at the specified location.
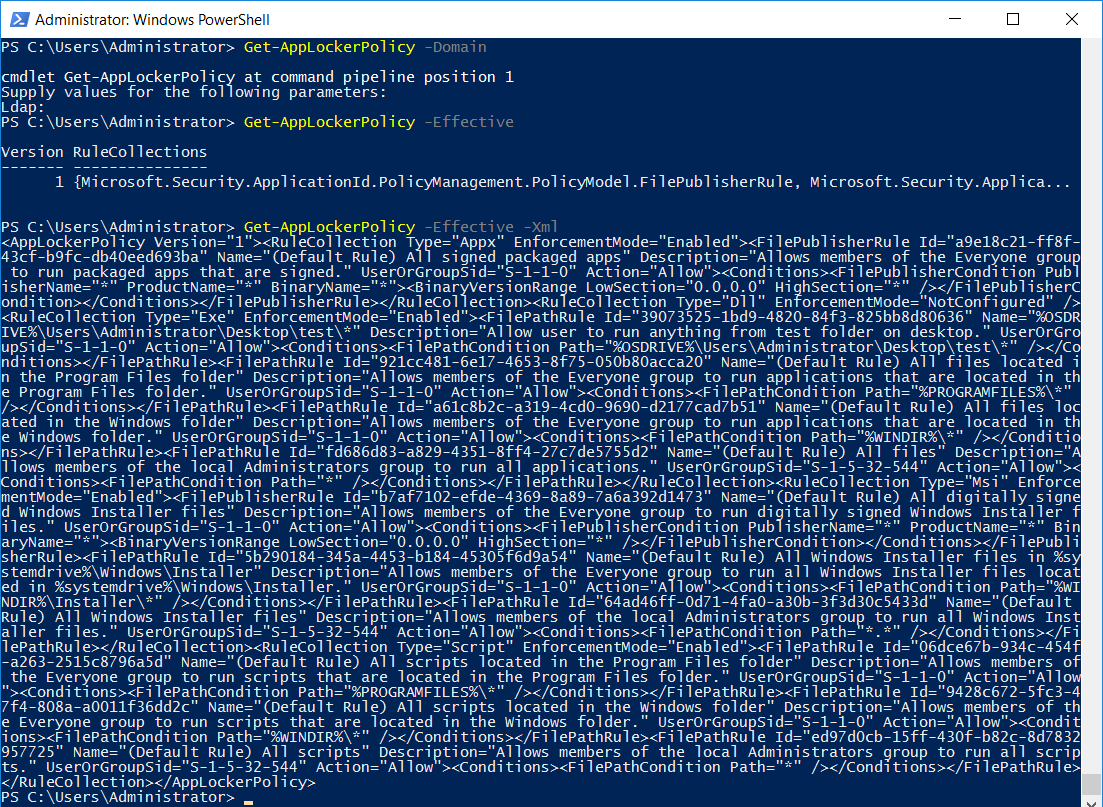
- Get-AppLockerPolicy: This cmdlet is used to retrieve local, effective, or a domain AppLocker policy. We can specify a local policy with the -Local option, domain policy with -Domain followed by the LDAP path to the policy, or -Effective to view the effective and applied policy. We can also specify -Xml to output the results as an XML value, the example below demonstrates this allowing us to see what our AppLocker policy is doing through PowerShell.
We can also send this out to a .xml file by adding ‘> C:\file.xml’ on the end.
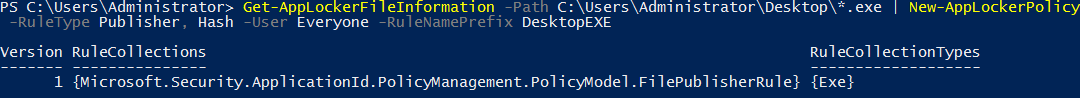
- New-AppLockerPolicy: This cmdlet creates a new AppLocker policy from a list of specified information, the information can be viewed by running Get-AppLockerFileInformation as shown previously.
- Set-AppLockerPolicy: This cmdlet sets the AppLocker policy for a specified group policy object. We noted how to create an XML file using Get-AppLockerPolicy cmdlet previously, this is the sort of file that can be sent into Set-AppLockerPolicy.
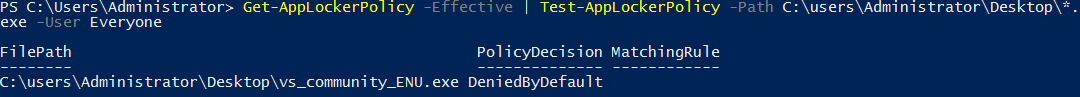
- Test-AppLockerPolicy: This cmdlet is used to determine whether or not a specific user or group of users will be able to perform an action based on the policy, essentially allowing us to test the AppLocker policy. For instance in the below example we can check if the effective policies applied to this machine allow the user Everyone access to .exe files on the administrators desktop, in which case this is denied by default.
PowerShell Help
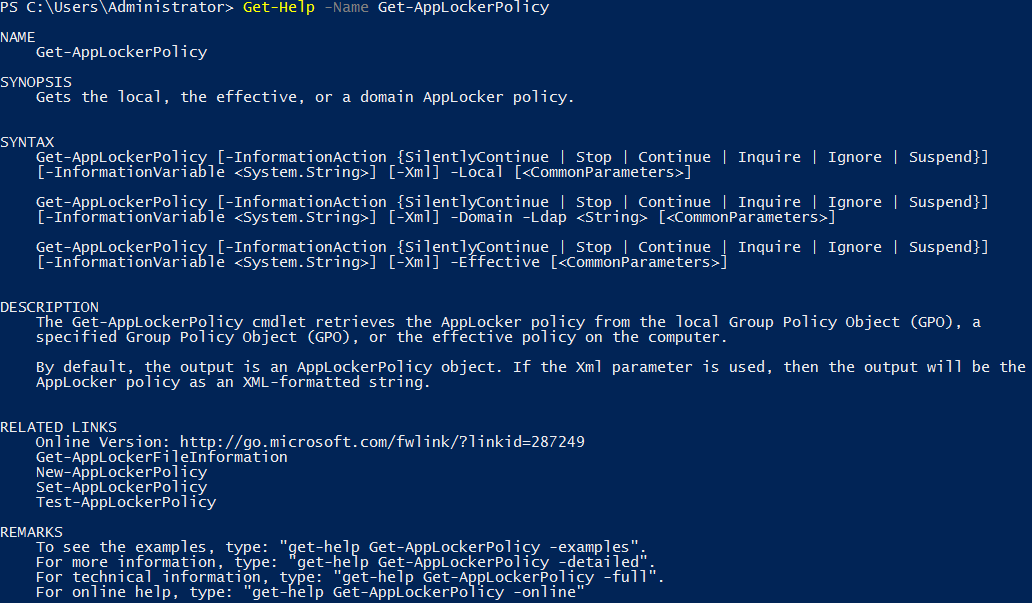
Note that if you forget what any of these cmdlets do, you can always use the ‘Get-Help’ cmdlet to view useful information. We can also add in -Full, -Examples, or -Detailed for even more documentation.
Summary
As you have seen we can implement AppLocker rules using Windows PowerShell. While this is possible, the PowerShell cmdlets are intended to be used in addition to the graphical user interface to set local or domain based group policy in your environment.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
how would I write a PowerShell command to block the installation of Firefox?