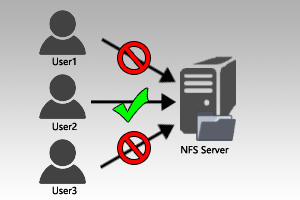
Most of us would be familiar with the simple ICMP based ‘ping’ command which allows us to test for a basic response from some network connected device. While great for basic troubleshooting it does not allow us to confirm if the particular host at the other end is responding on TCP or UDP ports where the majority of services are likely to be provided.
Ping isn’t the be all and end all of network troubleshooting, if a firewall blocks inbound ICMP traffic then a ping will not succeed which can produce a false perception that the host is down as it is not responding to the ping, however other services could still be responding fine.
Alternatively while ping may come back fine with a response it doesn’t indicate if a web server is responding on port 80 for HTTP requests, the web server may have failed and no longer be responding.
So if ping is ICMP based, can we hit a TCP or UDP port for response instead? The answer is yes, let’s take a look.
Read more »