In Windows Server 2016 we can secure DNS traffic using DNSSEC and DNS policies. DNSSEC allows a client to validate DNS responses, as by default DNS was not designed to be a secure protocol. DNSSEC allows a client to confirm that the information which has been returned from a DNS server has actually come from the correct and trusted DNS server without modification.
DNSSEC, which stands for Domain Name System Security Extensions, was added to help secure the existing DNS protocol. This guide will walk you through configuring DNSSEC in a Windows Server 2016 environment.
It’s also important to note that DNSSEC is not something unique to Windows, it’s an extension to DNS and is therefore operating system agnostic. I suggest this guide if you’re after an overview of DNSSEC, as the rest of this post will outline how to configure and use it, rather than provide specifics on all the DNSSEC records. It should also be noted that in order for a DNS server to use DNSSEC it must be running Windows Server 2012 or newer.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Secure DNS Traffic Using DNSSEC and DNS Policies
We’ll start by discussing how to secure DNS traffic using DNSSEC, then move on to using the Name Resolution Policy Table (NRPT) to ensure that clients use DNSSEC for specified domains via group policy.
Configure DNSSEC
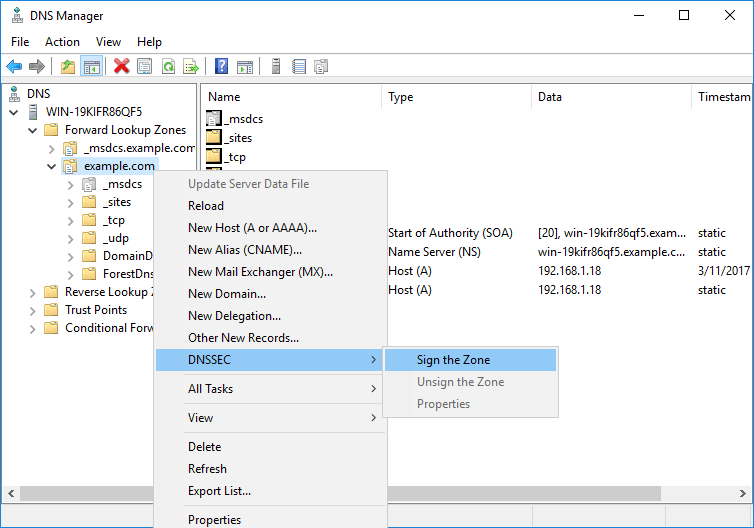
In this example we’ll be configuring DNSSEC on an active directory domain controller which is already acting as a DNS server within the domain. Start by opening DNS Manager, this can be found in Server Manager under Tools > DNS.
In DNS Manager select Forward Lookup Zones and find the DNS zone that you want to sign. In this example, this is example.com. Select DNSSEC, followed by sign the zone.
This will open the Zone Signing Wizard, click next to proceed.
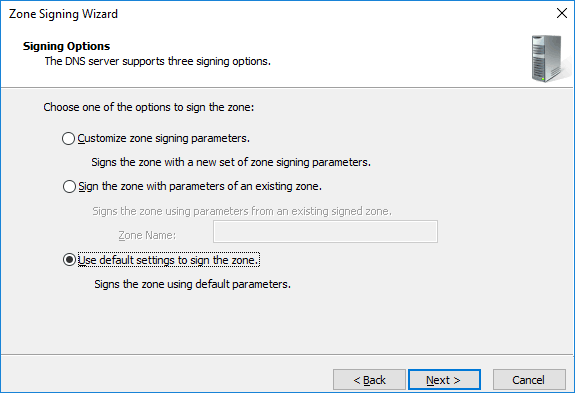
While we can customize the settings, in this example we’ll stick to the default settings when signing the zone.
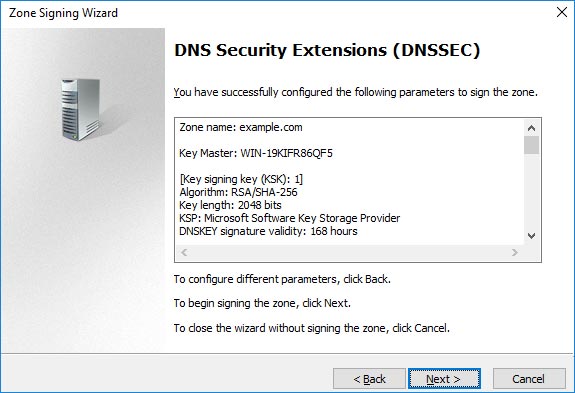
We’ll now be presented with the parameters that will be used when signing the zone, you can scroll through these then click next to continue.
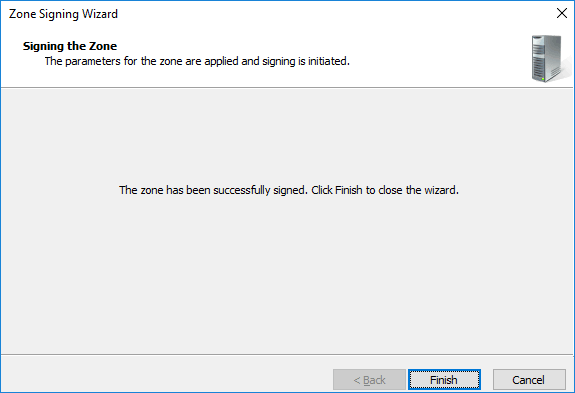
You’ll then be advised when the signing process has completed, click finish to complete the process.
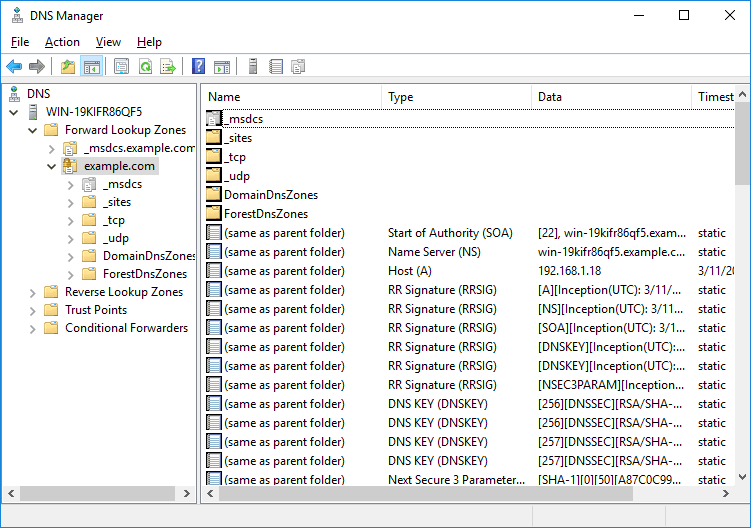
We can now refresh the DNS Manager window and see that we have a whole bunch of DNSSEC related records now showing.
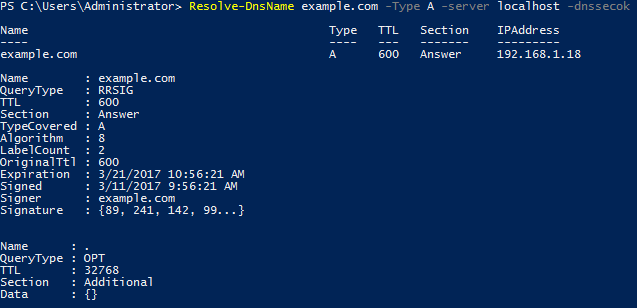
Alternatively PowerShell can be used, namely the Resolve-DnsName cmdlet. As shown below with the -dnssecok option we can view some information specific to DNSSEC that was not there prior to signing the zone.
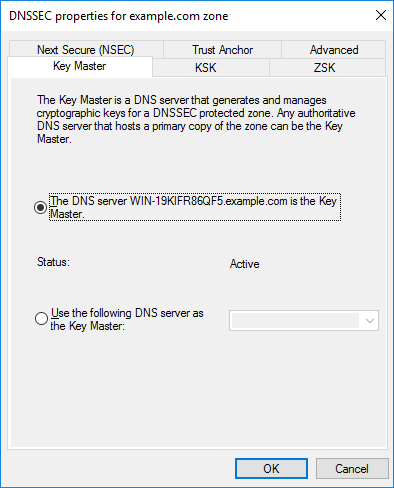
We can also view the DNSSEC properties by right clicking the zone, selecting DNSSEC as before, followed by properties.
Configuring the Name Resolution Policy Table
Now that DNSSEC has been configured and the zone has been signed, we’ll configure the NRPT through group policy.
To begin open up Group Policy Management, this can be done either through Server Manager > Tools > Group Policy Management, or by running ‘gpmc.msc’ in PowerShell or Command Prompt. At this point you can either create a new policy, or edit an existing policy. In this example we’ll create a new GPO called “DNSSEC”.
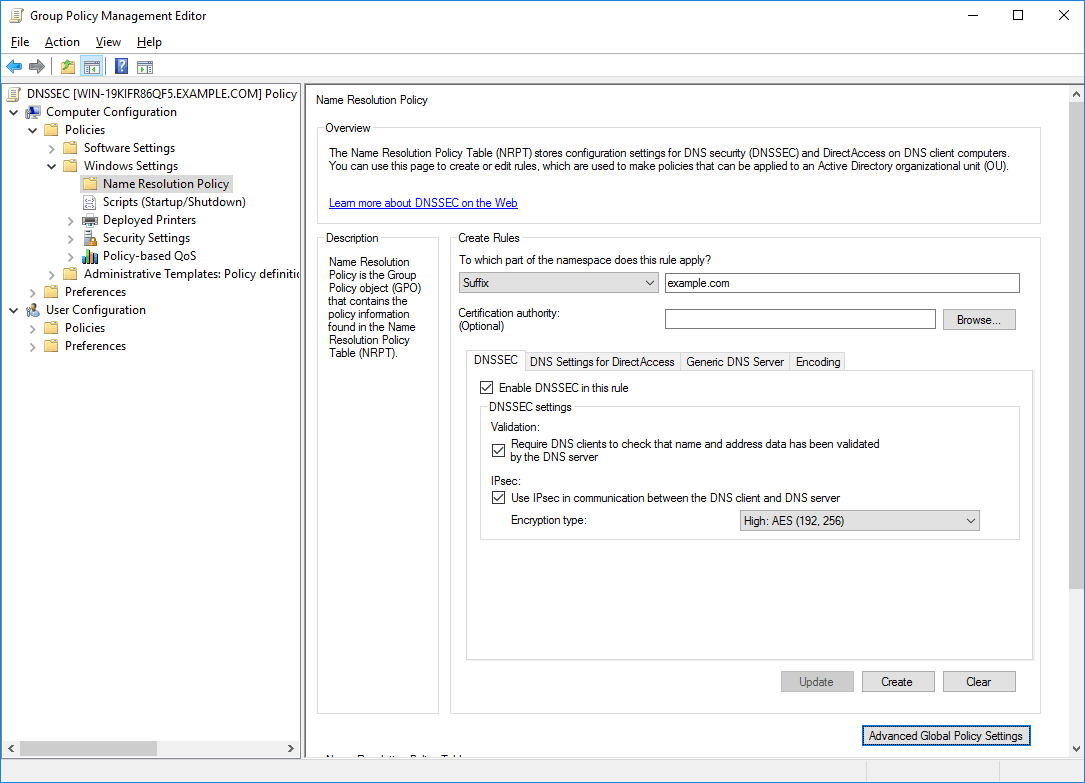
Edit the policy, and browse to Computer Configuration > Policies > Windows Settings > Name Resolution Policy.
In this example we are configuring all DNS resolution for the *.example.com domain to require that clients use DNSSEC over IPsec, which will also encrypt the server between the DNS client and server. DNSSEC alone does not encrypt the actual DNS traffic, however we can do this with the help of IPsec. Once you’ve set things how you like, scroll down and click apply. All that’s left to do is apply the group policy object (GPO) to a site, domain, or organizational unit (OU) where you want the policy to effect.
Implementing DNSSEC does introduce a performance overhead, check out the DNSSEC performance considerations page from Microsoft if you’re interested in this.
Other DNS Security
There are some other DNS security features that Microsoft have implemented to help secure a DNS server.
DNS Cache Locking
DNS records are cached for the period defined in the Time To Live (TTL) value defined in the record. If the TTL expires, the record will be removed from the cache until it is looked up and cached again. Caching records helps improve DNS performance as the DNS server will not need to perform a lookup to an external DNS server.
DNS cache locking can help protect the DNS cache from poisoning attacks by locking the cache, preventing entries from being overwritten. By default DNS cache locking is enabled, and will lock the cache for the entire period that a record is cached. The below command will change the cache locking percent to 50%, meaning that after a record has passed 50% of its TTL it can be modified.
dnscmd /config /cachelockingpercent 50
Note that the default value of 100% is preferable in most environments, the above command is for demonstration purposes.
DNS Socket Pool
This is another DNS security feature however this time it’s specific to Windows Server 2008 R2 and newer. This will make the DNS server use a random source port when sending out DNS queries which helps protect against DNS cache poisoning. As the source port is now random for each DNS request rather than the same and more predictable it’s harder for an attacker to guess correctly. This is enabled by default to use 2500 different ports, however we can expand this up to a maximum of 10000 with the dnscmd command.
dnscmd /config /socketpoolsize 10000
Summary
We can secure DNS traffic using DNSSEC and DNS policies in our Windows domain to provide origin authority, integrity of data, and authenticated denial of existence and help protect against DNS spoofing attacks. With group policy we can configure the name resolution policy table to ensure that clients use DNSSEC when resolving DNS to specified domains. We can even optionally encrypt this traffic with IPsec, as DNSSEC in itself does not offer any encryption to the DNS traffic.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
0 Comments.