NT Lan Manager (NTLM) is a proprietary Microsoft security protocol for providing authentication in the Windows operating system. It’s quite old, and we can implement NTLM blocking to disable it, allowing us to increase overall security by instead moving to another protocol such as Kerberos. We’ll see how to do this in Windows Server 2016 using group policy in the examples here.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
About NTLM
NTLM is still used for computers that are members of a workgroup as well as local authentication. In an Active Directory domain environment however, Kerberos authentication is preferable.
From Windows Server 2003, Kerberos has been suggested rather than NTLM as it’s a stronger authentication protocol which uses mutual authentication rather than the NTLM challenge/response method. NTLM has a number of known vulnerabilities, including that it uses weaker cryptography and has no server authentication. It’s possible to bruteforce a length 8 password using NTLM in just a few hours, and NTLM is also vulnerable to the pass the hash attack.
For these reasons it’s important to consider moving over to Kerberos based authentication if possible and disabling NTLM, however NTLM may still be required for legacy purposes which you should first check.
Implement NTLM Blocking
With group policy we can disable the older NTLM and only allow Kerberos, this is known as NTLM blocking. Before doing this however, you should check and ensure that both Microsoft and third party applications in your network do not require NTLM authentication before proceeding. You can follow this guide from Microsoft to help determine where NTLM may be used within your environment.
The group policy options for NTLM are found under Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
Restrict NTLM in the Domain
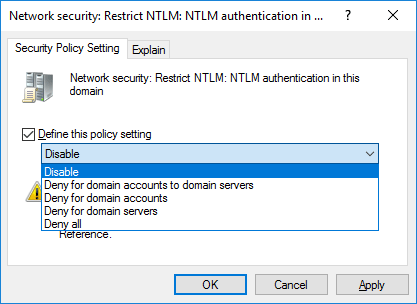
In particular we’ll start by looking at the “Network Security: Restrict NTLM: NTLM authentication in this domain” policy.
Once the policy has been selected, we can tick to define it and then select an option from the drop down menu as shown below. This policy allows us to allow or disable NTLM authentication within the domain.
- Disable: This disables the policy, and allows NTLM authentication within the domain.
- Deny for domain accounts to domain servers: The domain controllers within the domain will deny all NTLM attempts to all servers in the domain using domain accounts and return an NTLM blocked error.
- Deny for domain accounts: The domain controller will deny all NTLM authentication attempts from domain accounts and return an NTLM blocked error.
- Deny for domain servers: The domain controller will deny NTLM authentication requests to all servers in the domain and return an NTLM blocked error.
- Deny all: The domain controller will deny all NTLM pass-through requests from its servers and for its accounts, returning an NTLM blocked error.
Rather than configuring all NTLM authentication in the domain, we can also work with the “Incoming NTLM traffic” and “Outgoing NTLM traffic to remote servers” policy items.
It should also be noted that this policy is supported in Windows 7 and Windows Server 2008 R2 or newer.
NTLM Exceptions
There is an exception to the above, and that is the creation of a specific exception. We can explicitly allow NTLM authentication by setting either the “NTLM security: Restrict NTLM: Add server exceptions in this domain” or “Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication” policy. This allows us to disable NTLM everywhere, with the exception to what we specify.
Be Careful
As Ned Pyle notes in this NTLM analysis blog post, when you implement NTLM blocking it can be a resume changing event, so be careful and plan it out. Make use of the “Network security: Restrict NTLM: Audit NTLM authentication in this domain” policy first and monitor the logs over a period of time to assess if any applications are using NTLM and create a migration plan before you implement NTLM blocking.
Note that this process does not completely disable NTLM on the machine, as mentioned NTLM is still used for local accounts and these will continue to work with NTLM disabled through group policy. This behaviour is expected, as your local machine is not a domain controller or Kerberos key distribution center (KDC).
Summary
If you implement NTLM blocking in Windows Server 2016, we can disable NTLM and increase our security in a domain environment by instead using Kerberos for authentication. This is done through group policy, however be careful and first check if any applications rely on NTLM before proceeding.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
0 Comments.