We can implement auditing using Windows PowerShell with the Get-Acl and Set-Acl cmdlets. These allow us to view and modify the auditing options of a file or folder in Windows. While this can also be done through the graphical user interface, using PowerShell allows us to script such actions, as well as some extra functionality such as copying the auditing settings from one object to another.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Implement Auditing using Windows PowerShell
We can use PowerShell to view and set System Access Control Lists (SACLs) with the Get-Acl and Set-Acl cmdlets respectively. While we need to enable auditing policy through group policy or using auditpol.exe, that’s only half the story. We also need to define auditing on the file, folder, or active directory object itself so that events related to it will be logged. As covered in the guide linked, we’ve been setting this through the graphical user interface. We can also use PowerShell to set these items.
Using Get-Acl
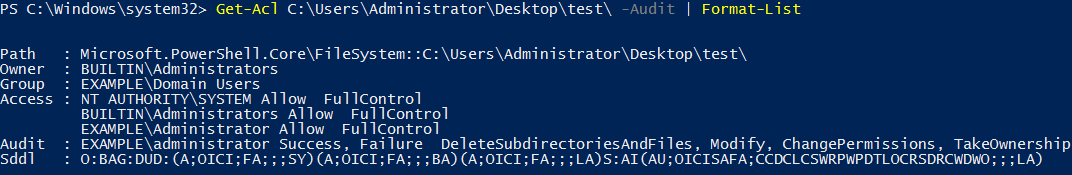
The Get-Acl cmdlet is fairly straight forward to use, in this example we simply specify a folder after it to view the permissions assigned followed by the -Audit option to only display auditing information. We pipe the output into Format-List so that we can see it all.
We can see that the “Audit:” section lists what we are currently auditing for, which is administrator success or failure access to this folder.
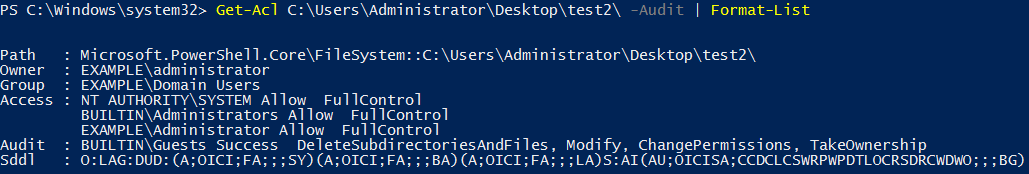
We also have a test2 folder which we are currently auditing for when users in the guest group successfully access the folder.
Using Set-Acl
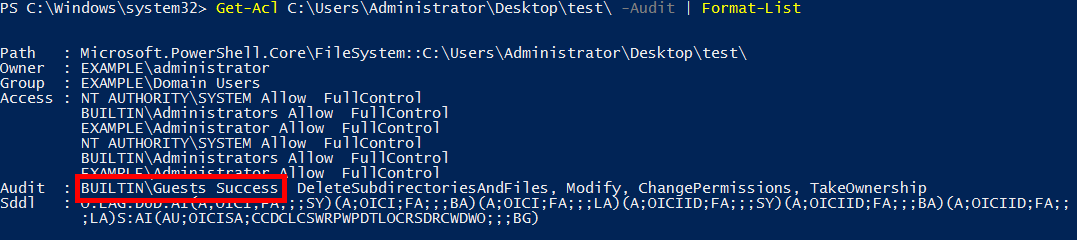
In this example we’ll use the Set-Acl cmdlet to copy the audit settings from test2 to the test folder. As shown below we simply use Get-Acl to get the auditing specific entries from the test2 folder, then pipe the results into Set-Acl which applies them to test.
When we run Get-Acl on the test folder after this, we can see that the new audit settings are showing the same as test2. Note that this has removed the original settings applied to the test folder.
Note that if we don’t specify the -Audit option, all settings will be copied over which may not be what we want.
Other
We can also use PowerShell to run the auditpol.exe command although that doesn’t directly implement auditing using Windows PowerShell.
While this exam objective was meant to cover enabling auditing using PowerShell, we can also enable auditing for PowerShell which allows us to log PowerShell commands that are run.
Summary
As you have seen there isn’t really anything too important with regards to the “implement auditing using Windows PowerShell” 70-744 exam objective. We can use the Get-Acl and Set-Acl PowerShell cmdlets to set auditing on files and folders, however the relevant audit policy still needs to be configured through group or local policy. Otherwise we can use PowerShell to run auditpol.exe however we can run that through Command Prompt too.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
0 Comments.