We can implement auditing using group policy and auditpol.exe in Windows Server 2016. This will allow us to log very specific events that take place within the operating system. We’ll demonstrate how to configure audit policies with both of these methods here.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Implement Auditing Using Group Policy
As is common in Windows, group policy is the easiest way to implement auditing automatically throughout our domain. Group policy allows us to define the auditing settings that we want and then deploy them to a select group of machines or users.
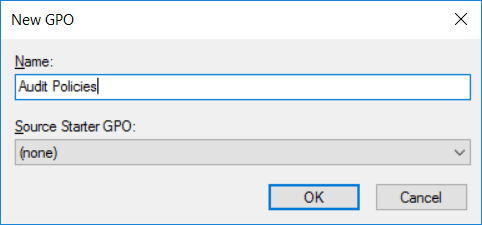
To begin open up Group Policy Management, this can be done either through Server Manager > Tools > Group Policy Management, or by running ‘gpmc.msc’ in PowerShell or Command Prompt. At this point you can either create a new policy, or edit an existing policy. In this example we’ll create a new GPO called “Audit Policies”.
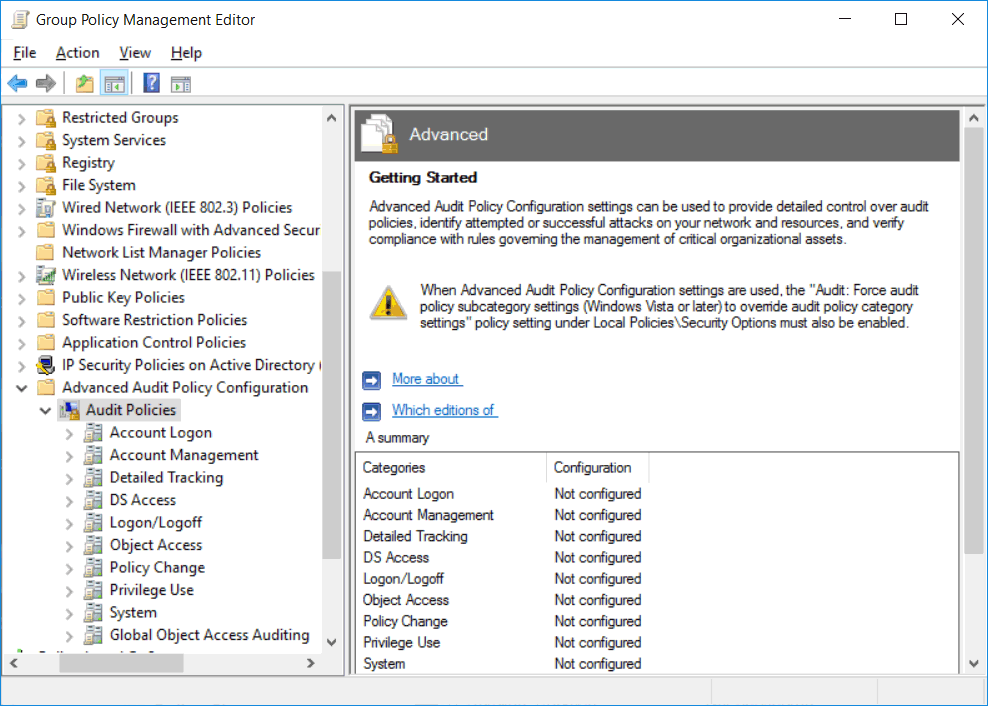
Within the policy navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies. From within here you should be able to see all of the available advanced audit policies.
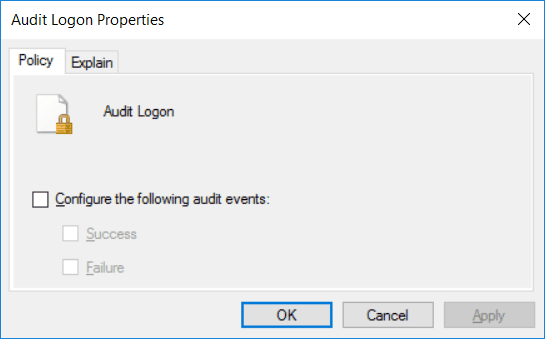
Within each of these are the actual policies themselves, there are more than 60 and they allow you to be very granular and specific. Either double click a policy, or right click it and select edit to view the properties. To enable the audit policy, all you need to do is select the “Configure the following audit events” checkbox, followed by specifying if you want to audit for success, failure, or both types of events. For specific information on what the policy does you can refer to the explain tab.
Once you’ve set everything that you wish to audit, apply the policy to the site, domain, or organizational unit (OU) that contains the computer objects that should receive the policy.
Depending on the audit policy in use, there may be some additional steps needed. For example if we enable auditing for access to a file or folder we also need to configure auditing on that file or folder too. This allows us to specify which users or groups we actually want to audit for. The same goes for an audit policy that applies to active directory based items, we need to enable auditing on the specific item in a similar manner.
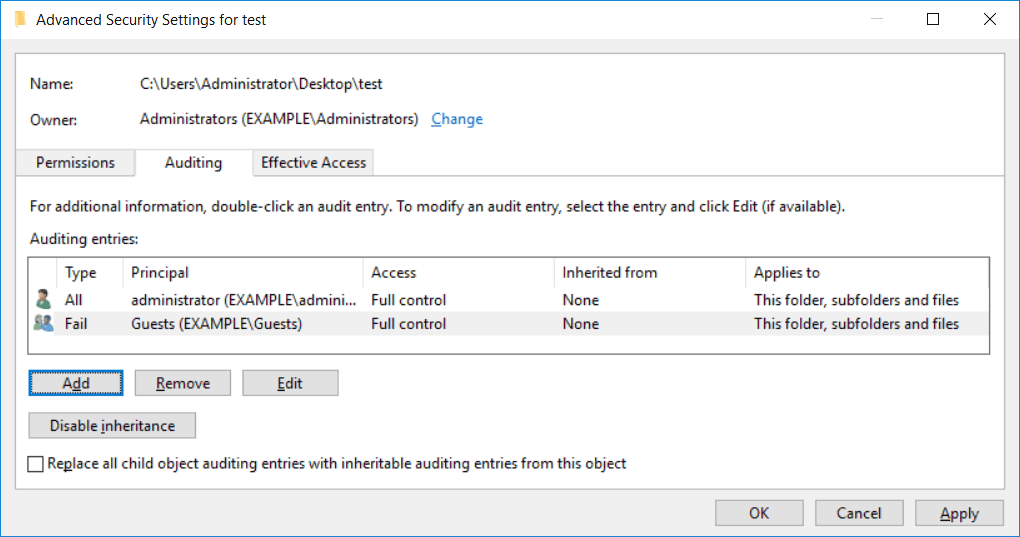
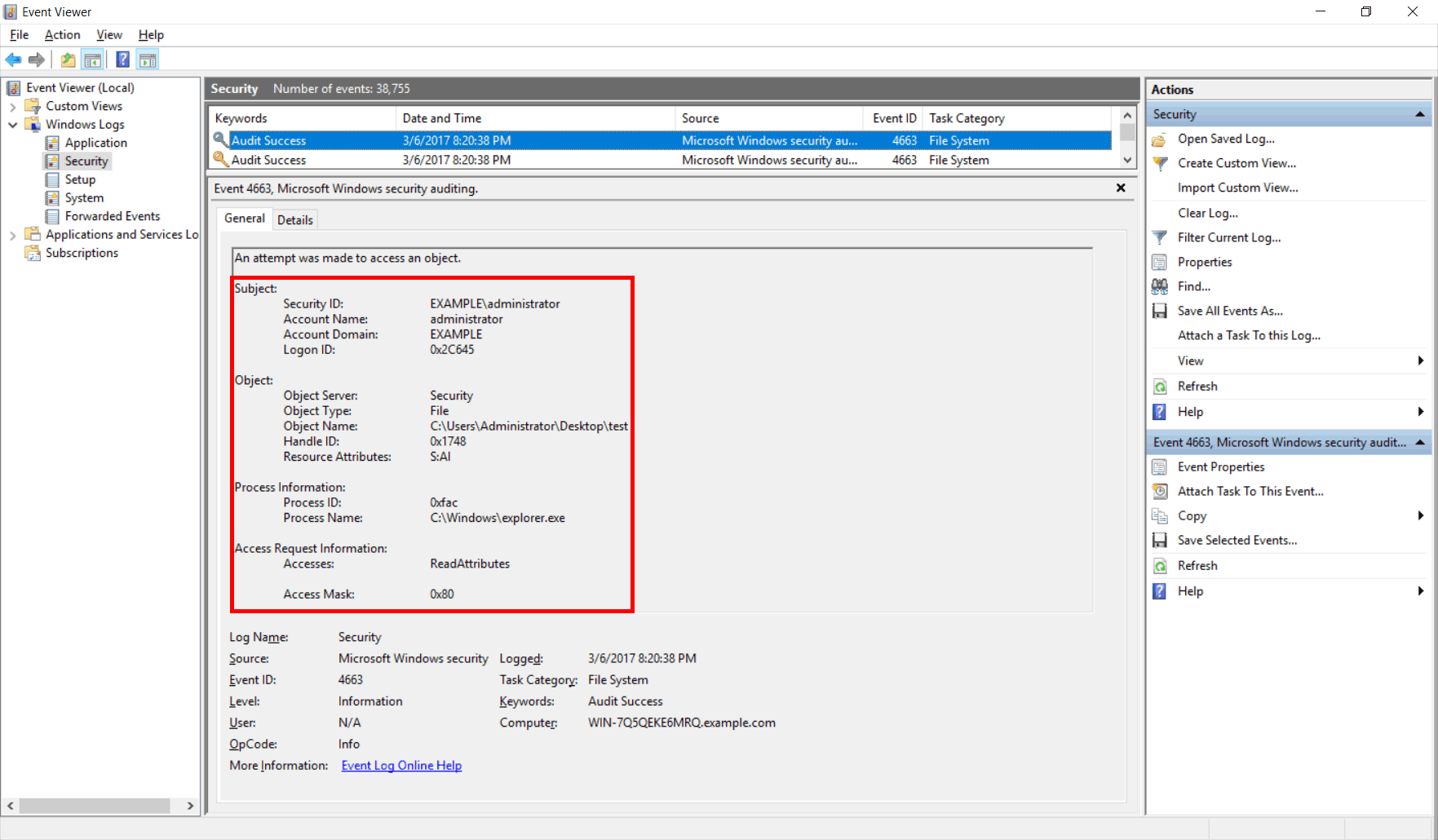
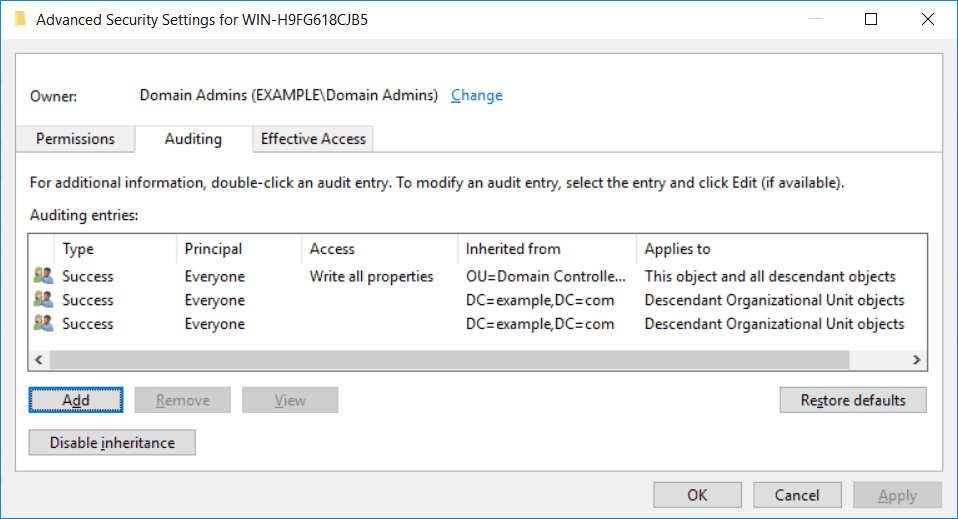
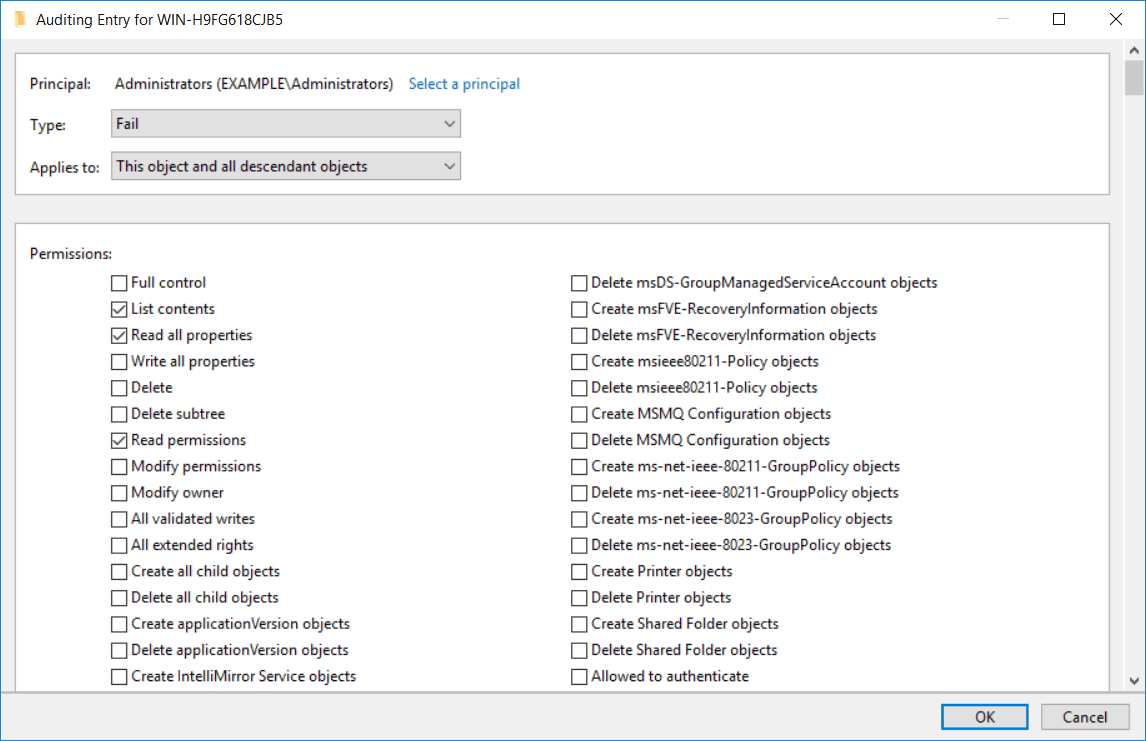
For example, right click a file or folder and select properties. Select the security tab, then click advanced. In the advanced security settings window, select the auditing tab. You can now add users or groups that you want to audit, along with the permissions that you want to audit for.
Once complete events can be viewed through the security event log in event viewer.
We can also configure auditing on Active Directory based events in a similar way if you configured an audit policy that works on these objects. Simply view the properties of an object through Active Directory Users and Computers and select the security tab, note that to see this you’ll need to select View > Advanced Features. The rest of the process is similar to the file or folder process, from the properties window select the security tab, click advanced, then auditing.
We can then add a new auditing entry. As you can see there are a lot more items to choose from here, you can be extremely granular when configuring auditing on Active Directory based objects.
Implement Auditing Using AuditPol.exe
The AuditPol.exe command is used to view the auditing policies in place on a user or computer. Additionally it can be used to create, configure, or remove an audit policy. As AuditPol.exe must be run on each individual computer to modify the local policy rather than group policy, the process is much more manual compared to the group policy method described above.
You can find the full documentation for auditpol.exe here.
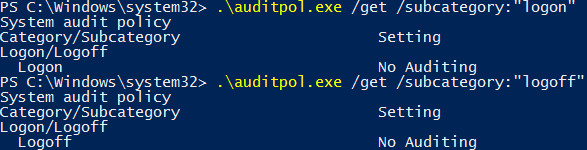
As per the documentation we can use the /get option to display current audit policies, while /set is used to configure audit policies.
We can also use /backup to save a copy of the local audit policies in place to a file, and /restore to read the contents of that file in to import the policies. We can also remove all audit policies in place with /clear.
By default some of the advanced audit policies that we showed earlier are enabled in Windows. These do not show through the group policy window however, we can instead use auditpol to view the default policy settings currently in place. This is an example of why we need to implement auditing using group policy and auditpol.exe to view some of the changes, especially for dealing with and setting local policy.
Summary
We have shown you how to implement auditing using group policy and AuditPol.exe in Windows Server 2016. We can use group policy to apply audit policy changes to a set of computers within a domain automatically, however we still need to manually modify the security settings of files, folders, and domain objects. We can also use AuditPol.exe to work with local audit policies, note that these changes are only local within the Windows operating system they are applied to.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Is there a way to use Domain Policy to set a file/folder audit policy WITHOUT modifying the permissions of that object? I was able to successfully set the audit policy of client computers, but it unfortunately updated the permissions and caused issues for the user.