This guide will show you how to increase the security of an Invision Power Board (IPB) installation. We’ll walk through practical examples for you to follow to harden IPB, reducing your attack surface.
There are a lot of insecure default options which unless modified will put you at a higher risk of being compromised by an attacker. Here we will outline what should be modified to increase security of IPB.
In these example we’ll be working with Invision Power Board 4.1, so while any specific locations of items or screenshot contents may change over time, the general concepts should still remain valid even after future updates. For items in the Admin CP, you can always use the search box to find them if the graphical user interface changes. Due to this most of these recommendations also apply to version 3.x.
Invision Power Board Security Tips
Rename Admin Directory
By default the Admin CP is available at http://example.com/admin which is widely known by attackers and easy to discover. Invision Power Board supports renaming the Admin CP directory in order to hide it. While this is merely security through obscurity, it does make it more difficult for the location of the Admin CP to be found.
How this will actually be done will depend on your web host, it may be possible to complete through a control panel such as cPanel or Plesk, or otherwise it can be done through SSH. Please contact your hosting provider should you need assistance with renaming the admin directory.
In the Linux command line, this can be done with the ‘mv’ command which will essentially rename the default admin directory to what ever we specify. In the example below, the admin directory is renamed to g78Gq7LevUDzA3b.
mv admin/ g78Gq7LevUDzA3b
Make sure that you choose some other random string to use for the directory, g78Gq7LevUDzA3b is an example and it would not be ideal if everyone reading this post changed to the same name! Anything over length 10 or so should be fairly safe from brute force guessing attacks.
Remove Admin CP Link
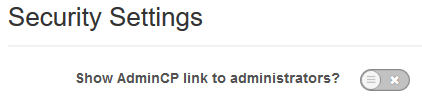
Now that the Admin CP directory has been changed from the default, it’s also a good idea to hide the link. By default when a user with admin permissions logs in, they are provided with a link to the Admin CP which will reveal the location of the custom directory.
We can defend against this by removing the Admin CP link, this way even if an attacker does compromise an administrator account they will not have a link to the Admin CP, and if the path to it has also been changed they will not be able to find the login page. This is done through the Admin CP > Security Center > Security Settings, as shown below you simply click the button to change it.
If you have other admin users that need to access the Admin CP legitimately, you’ll just have to advise them of the full URL in advance so that they can bookmark it or otherwise keep a record of it. It would not be advisable to send the information out through Invision Power Board itself either, as an account compromise could result in forum threads or private messages being read. Instead send the details via some other out of band method if possible.
Add Additional Password To Admin CP
By default when you load the Admin CP page, you will be prompted for the username and password combination for your forum account. Assuming the account has administrative privileges, you will be logged into the Admin CP. Unfortunately if an administrative forum account is somehow compromised, these same credentials can also be used to log into the Admin CP.
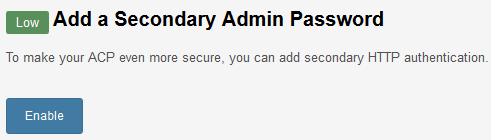
Therefore it is recommended to add an additional password to the Admin CP page with htpasswd. Essentially this will prompt for a username and password combination before even loading the Admin CP login page. The credentials are not stored as part of the Invision Power Board software either, so even if all user accounts are somehow compromised they will not get the htpasswd credentials.
Invision Power Board provides a useful built in method of creating this into the .htaccess file through the Security Center. Simply go to System > Security Center, and if not already enabled you will see the below message about this. Simply click the enable button and the .htaccess file will be created automatically with the password you choose.
Additionally .htaccess is not automatically read by all web servers, in Nginx we can use configuration similar to the below to perform this for us.
location ~^/g78Gq7LevUDzA3b/ { auth_basic "Password Protected Area"; auth_basic_user_file /etc/nginx/.htpasswd; location ~ \.php$ { try_files $uri =404; fastcgi_pass unix:/var/run/php-fpm/php-fpm.sock; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; include fastcgi_params; } }Once the configuration is in place, we’ll use the ‘htpasswd’ command to create a new file at /etc/nginx/.htpasswd. Note that the -c option should only be used the first time as it will create a new file, do not use it once the file already exists as it will overwrite the whole file.
htpasswd -c /etc/nginx/.htpasswd username
Only Allow Specific IP Addresses To Admin CP
Likewise we can also modify the .htaccess file or web server configuration to only allow a specific list of trusted source IP addresses into the Admin CP area. Depending on the amount of admin users you have, and the locations they require access from, this may not be feasible. Be sure to replace <your ip> with your actual IP address.
order deny,allow deny from all allow from <your ip>/32
Again if you’re using Nginx this can be done in the Nginx configuration as shown below.
location /g78Gq7LevUDzA3b { allow <your ip>/32; deny all; }If your Admin CP only needs to be accessed from a few static IP addresses only however, then this is a very good security measure to put in place as all other access attempts will simply be denied.
Restrict Admin User Privileges
By default the privileges that an admin has are extremely powerful, it’s highly likely that not all users will need access to every single function of Invision Power Board so it is recommended that they be restricted and denied from doing anything that they do not need in order to perform day to day duties.
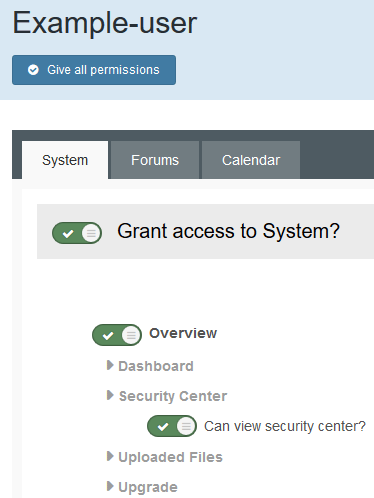
Essentially it’s best practice to assign the lowest level of permissions required to each user/group. To edit what administrative users can access within the Admin CP, go to Members > Administrators (under Staff) and select edit on any of the administrators. From here you will be able to enable or disable specific permissions. Note that there are a lot more of these than the few displayed in the image below, they are worth going through and restricting.
Some of my favourite examples of things to disable access to are as follows.
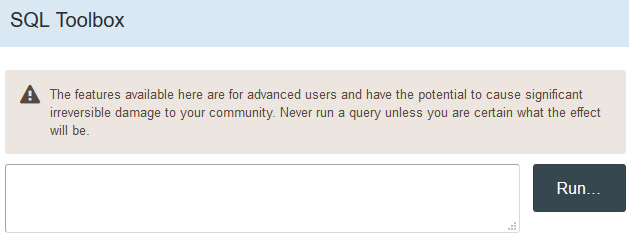
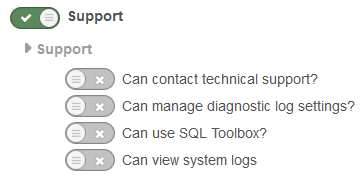
SQL Toolbox
This allows an administrative user to perform queries against the database through the web interface. This is extremely powerful and allows for all sorts of information to be exported, including usernames, password hashes/salts and email addresses to name just a few.
The permission to disable is “Can use SQL Toolbox?” and is found under Support.
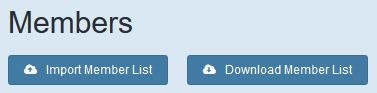
Export Member List
This is similar to the above, a user with this access is able to simply export a copy of the entire member list as a CSV file, along with what ever they desire such as usernames and password hashes/salts.
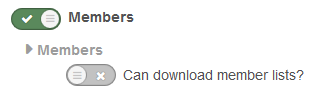
The permission to disable is “Can download member lists?” and can be found under Members.
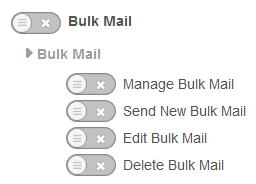
Bulk Mailer
On my websites, not all administrators need to be able to send bulk email messages out to all members, so this is disabled. In the past I have seen this used to send out a phishing campaign from a compromised admin account, so better to disable it if not needed. The permission to disable is “Bulk Mail”.
These are just some of the worst things that you want an attacker to gain access to, it is advised that you look through all of the specific granular permissions in this area and assign the least amount of privileges to users and groups as possible.
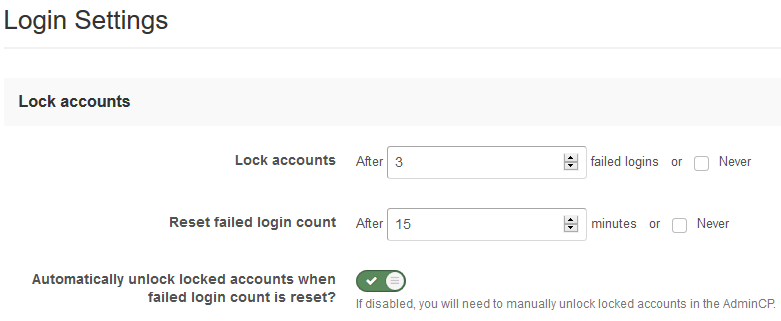
Account Lockout Settings
Account lockout is enabled by default, however you should review the default settings and tweak them if needed. These settings are accessed through the Admin CP > System > Login Handlers > Login Settings. This will help defend against brute force login attacks, as an account will be locked out from access after just a few attempts.
Use Strong Passwords
While this may seem like an obvious point, it’s still very important to get across nonetheless. You should be operating on the assumption that eventually your database will be captured by an attacker, and when that day comes they will have full access to all hashed user passwords and salts. These can then be further attacked offline and broken, providing further user accounts to the attackers, which if reused on other websites can be used again and again elsewhere further down the track.
Passwords should be long, unique and not used anywhere else. While this is impossible to practically enforce, all users should be made aware of it as part of your websites password policy and should make an effort to follow through.
While user passwords are hashed and salted, they can still be cracked quite quickly with hash cracking programs such as Hashcat. I’ve found that password length works very well at putting a stop to these attacks.
Minimize Additional Plugins, Applications Or Themes
There are a large number of plugins, applications, and themes available for installation in Invision Power Board that provide lots of useful additional features and functionality. This however creates a problem, as essentially anyone can create a third party plugin, application, or theme it gets harder and harder to ensure that what you’re installing is secure and does not have vulnerabilities that can be exploited by an attacker.
The best thing you can do is install as few as possible. Using only required third party options that appear to come from a reputable source, are still actively maintained and have many positive reviews is usually a good sign.
Force HTTPS
If your Invision Power Board installation is accessed over plain text HTTP, every time a user submits their username and password through your website it is transmitted over the Internet for anyone watching to see. This is fixed by browsing with HTTPS, which requires a certificate in order to perform encryption of the traffic.
While this is a pretty unlikely attack vector as the attacker would need to be positioned on the network between the end user logging in and the web server, it does exist and is something to be aware of.
Luckily these days it’s quite easy to implement HTTPS, CloudFlare for example provide you with a free certificate and you can enable HTTPS with a few mouse clicks. Alternatively organizations such as Let’s Encrypt provide free certificates that are trusted in a wide range of popular browsers.
Disable IPB Version String
In older versions of Invision Power Board by default the currently installed version of the software is displayed toward the bottom of each page. This information is useful to an attacker, as it allows them to see the specific version of the software that you are running which lets them quickly perform a search to see if there are any known vulnerabilities that can be exploited.
Rather than handing this over so easily, we can easily disable the version text. The version is enabled or disabled in 3.x versions through the Admin CP > System tab > Security and Privacy > Privacy by setting “Display IPB version on your site?” to either yes or no.
Fortunately this is no longer the default, or even an option to change in IPB 4.x.
Two Factor Authentication
Out of the box Invision Power Board does not currently provide support for two factor authentication, however this function can be gained from a third party plugin. This would require administrators to log in with their password as well as a second factor of authentication such as a one time code.
While keeping in mind what was mentioned above about third party plugins, if you do require this feature be sure to pick a reputable plugin with decent reviews that is still actively supported and maintained.
Personally I have not looked too much into using these, as the administrators that access Admin CP on the websites I manage have all sorts of different devices and it would be too difficult to get them all using the same application on their computer or smartphone, however it may be something that you want to investigate.
Lock Down File/Directory Permissions
By default Invision Power Board files and directories are created with standard permissions, 644 for files and 755 for directories.
While this is fairly standard and may even be required depending on how your web server is configured, it is certainly not always needed and may leak important information to other users on the server.
For example the conf_global.php file that contains the database password has the permissions 644, meaning that the file owner has read/write, while the group and others have read only. In my case the file is owned by the web server user and group, which is the same user that PHP-FPM runs as. Therefore I have no need for all other users to also be able to read the file.
This could happen if some other user has SSH access, they would be able to simply view this configuration file by default and retrieve the database password and possibly then connect to the database and dump it. I’ll use an example from a previous penetration test that I’ve performed to demonstrate this.
In this particular instance, the web server had the database port available over the Internet and it was possible to gain access to the database as a poor password had been selected. From the MySQL command line I was then able to read the conf_global.php file as the mysql user (or any other user at all for that matter) has read permissions on this file by default. Essentially if possible review the permissions of important files such as conf_global.php and ensure that only the web server and PHP users can access it, as these should be the only ones that require legitimate access.
Most shared hosting will prevent this with things such as suhosin, but new administrators setting up a web server on their own VPS are likely to run all websites as the default user of the web server. By doing this an attacker that compromises any website on the server will then be able to access files associated with other websites on the same server.
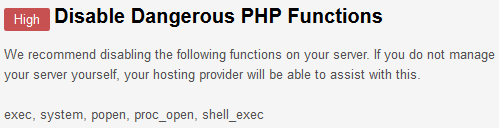
Disable PHP Functions
Unless you’re in a locked down shared hosting environment, you likely have all PHP functions enabled by default. We can see through the Security Center in the Admin CP that it is recommended that we disable the PHP functions exec, system, popen, proc_open, and shell_exec.
This is done by simply modifying the php.ini file and adding these to ‘disable_functions’.
disable_functions = exec, system, popen, proc_open, shell_exec
See this guide on finding where your php.ini file is located for further assistance.
Web Application Firewall (WAF)
While not strictly part of Invision Power Board itself, a web application firewall can help defend against various security issues. As mentioned previously, CloudFlare can be used to provide a website with HTTPS for free, however they also offer a WAF as part of their paid plans. While there are methods of bypassing the WAF and even CloudFlare itself, this will help keep out a lot of automated attacks.
Apply Security Updates As Soon As Possible
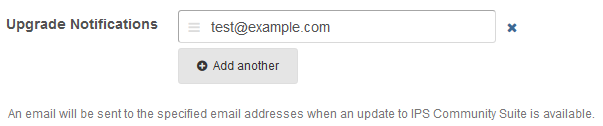
The Invision Power Board software receives fairly regular updates, and recently the update process has been made a lot easier. Simply log in and click a few buttons and the new files will be downloaded as needed. If you do not apply security updates as they become available, your installation of IPB will be running with known vulnerabilities which may be exploitable by an attacker.
Ensure that you have set an email address in the Admin CP for IPB to send emails to when updates are available, this way you can be alerted when updates are released and install them as soon as possible. You can check this through System > General Configuration (under Settings), or otherwise search for ‘upgrade notification’ in the search box.
Check Security Center
Through the Admin CP we can view the Security Center, which provides a useful overview of the security posture of Invision Power Board. Some settings can be modified through here, including removing the Admin CP link or enabling a password through the use of htpasswd as previously mentioned above, however any other security issues that IPB has identified will be listed here so that you are aware of them and can work towards fixing them.
Web Server Security
While the majority of the information here has been specific to securing the Invision Power Board software, keeping the web server itself secure is also extremely important. I have previously written a guide on securing Linux which covers many other topics that I recommend you read after this in order to ensure that your server is secured as can be.
Maintain Up To Date Backups
While not specifically a security measure, it is important that you keep your own regularly updated backup of the Invision Power Board files, and any associated databases in a safe and secure remote location (backups on the same server that the website runs off do not count). In the event that your website is compromised, having backups to restore from can save you a lot of time and effort when recovering. Of course when you do restore from backup, be sure that you patch what ever vulnerability that resulted in the website being compromised, otherwise it will just happen again later.
What To Do If You Have Been Compromised
While the above security measures should help protect your Invision Power Board installation, you should be aware of what to do if you discover that you have been compromised. This section is by no means an exhaustive list, but aims to simply provide a basic guide of things that you may want to consider doing should this happen. Your primary goal is to find out how access was gained and patch that hole, otherwise your cleanup efforts may be quickly undone.
Check The Logs
The logs are your best bet at getting an idea of finding out what happened. Both the web server and Invision Power Board logs through the Admin CP should be consulted. These will list when login events occurred, as well as from which IP addresses which you can then block.
Change Passwords
Changing the passwords of administrative users is a good idea, even if the logs do not indicate that an administrative account has yet been accessed. If the database or member list has somehow been breached it is possible that at a later date these user credentials could be cracked and used, so better to change them once you’ve fixed up what ever caused the compromise.
Currently there does not appear to be a built in method of forcing all users to change password with Invision Power Board, which is not ideal after a compromise. There are third party plugins available that offer this service, so that may be an option for you to consider.
Check Recently Modified Files
If you’ve been compromised it’s likely that files have recently modified. If you have SSH access you can quickly search all files by date recursively which should allow you to find files that have recently changed. Check these files for anything suspicious, particularly injected PHP strings. If you’re in doubt and you haven’t modified much of Invision Power Board, you can simply overwrite the file with a fresh copy from a clean copy of the Invision Power Board software – be sure to take a copy of any files you overwrite first, both for later analysis if required or simply if replacing the file breaks your website. Keep in mind that it’s not just files that can be modified, the database can also be modified to inject PHP into templates for example.
Contact Support
If you have an active Invision Power Board license you can contact their support team for further help and assistance if you require it. If your hosting plan provides technical support they may also be able to help you with recovering from a hack, though keep in mind that it is common practice for many of them to charge a restore fee for this service so you should ideally keep your own backup as outlined above.
While the software vendor and the web host should be able to help to some degree, they likely do not have extensive security expertise, so you may wish to track down someone who can help you properly discover any security holes that you have in your website such as an experienced penetration tester.
Summary
We have discussed a number of simple techniques that you can implement to increase the security of your Invision Power Board community website. In addition to these security measures, we briefly outlined some basic things to consider should your website be compromised.
Thank you for your tutorial, and for taking the time to make this resource for IPB admins. This was very helpful!
No problem!