Cloudflare is a freely available service that offers CDN and caching functionality. In order to use Cloudflare a domains DNS will be updated to send all traffic through Cloudflare, as a result it will hide the IP address of the actual web server where the website is hosted in order to provide various protections.
By doing this, Cloudflare essentially hides the real IP address of the web server that is hosting the website. There are many times that we may wish to be able to find the actual IP address of a server behind Cloudflare, such as during a penetration test you may want to bypass the web application firewall (WAF) completely by directly targeting the server itself.
The simple methods outlined here will show you how to find the real IP address of a website that is hidden behind Cloudflare. First we’ll cover the manual methods that can be used so that you understand what is going on before looking at automated options. Along the way we provide mitigations that can be used in order to protect yourself from these methods.
How To Find An IP Address Behind Cloudflare
Send An Email
This is my favourite method because it’s so easy and works very well. Essentially it involves having the web server send you an email, which should then contain the IP address of the server that sent it in the mail headers. Of course this may not always be possible, the website you’re trying to find the IP address of may not have any functionality that permits external mail being sent out.
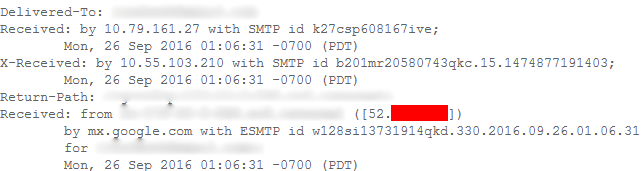
Some examples of this include registering an account on a website, using the forgot password form, or otherwise any activity that will cause the web server to initiate sending an external email to yourself. In the example below we can see the real IP address of the server that sent this message was from 52.x.x.x.
This can be mitigated if the server forwards to another server or service rather than sending out directly. Forwarding the email to another server to do the sending may help, so long as the email doesn’t leave via the public IP address of the web server otherwise this will still be recorded in the mail headers.
An example of this is if you had a dedicated mail server on an internal network with its own unique public IP address. The mail headers would show the internal IP address of the web server forwarding the mail to the mail relay, but the public IP address of the web server would not be recorded, only the public IP address of the mail server. Additionally there are also many services available that are able to send mail on your behalf which could again be used to stop mail leaving your web server directly.
Check DNS Records
If any DNS records are not configured to go via Cloudflare, they will point directly to the IP address of the server. We can use the dig command to check various DNS records on a domain and confirm whether or not they all point to Cloudflare or otherwise some other server which may leak the address of the server. This could be intentional or it may be a simple misconfiguration, an administrator may have a subdomain for testing purposes that traffic bypasses Cloudflare in order to avoid cached results, or it could just be a mistake that not all records go via Cloudflare. Some commonly used subdomains that are worth checking for this are ‘direct’, ‘direct-connect’, ‘ftp’ and ‘test’. Obviously there could be more, so be creative when searching.
The ‘direct’ subdomain used to be created by default when you added a domain to Cloudflare.
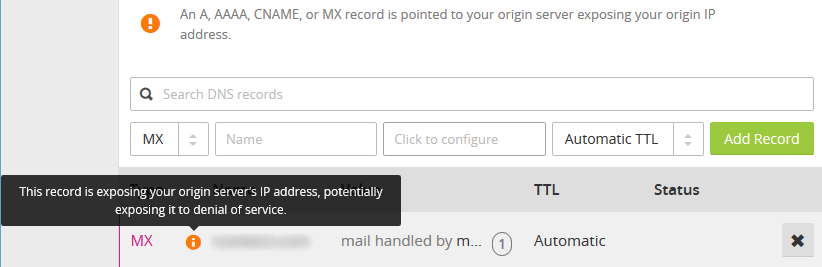
MX records for example always show the real mail server as Cloudflare does not hide this, therefore if mail for a domain is going through the same web server we can easily find it through the MX records.
Luckily as shown above, Cloudflare will alert us if we have any records that expose the IP address of our server. This can be mitigated by setting as many DNS records as possible to go via Cloudflare so that the real IP address of the web server is not leaked, though this may not always be an option depending on what you’re doing.
Check DNS History
If the website was not initially setup with Cloudflare enabled there may have been a period where DNS was pointing directly to the server. With the use of some online tools we can easily view the history of DNS records, which may reveal to us the IP addresses in use prior to Cloudflare being activated which may still be the same.
DNS Trails is one such website that seems to be fairly accurate in regards to the historical information that it maintains.
This can’t really be mitigated as the information is historical, however you could always request a new IP address from a different range from your service provider if it’s still the same. If you have Cloudflare enabled already and you update your records to point to the new IP the public DNS records will not change and the new address of the server should not be recorded anywhere publicly.
Automatic Lookup
Now that we have seen some of the manual methods that can be used to find an IP address that is hidden behind Cloudflare we’ll take a look at tools that provide automatic lookup.
The most popular option that I’ve found is Crime Flare. Based on the description it seems to work by checking for DNS records as mentioned above. They also maintain a large list of domains and their real IP addresses if detected. While this is a quick and easy option, personally I don’t think that it can compete with using all of the above manual methods which will provide better results with a little more work. For example, Crime Flare shows that this website is using an IP address from two years ago that is no longer in use, though they do note these limitations on the page so keep them in mind when searching.
Again this seems to be based off of DNS information, both current and historical. Therefore mitigations are the same as previously discussed, removing any direct DNS records or changing to a new IP address if the current address is stored as historical information.
Test And Confirm
Once you think you have the real public IP address where the website is hosted, how do you actually test and confirm that it is still correct?
A simple way to do this is to modify your hosts file and point the domain to the IP address, after flushing your DNS cache you can attempt to browse to that domain and it should still load up with the same page from the server if this is the real source of the website.
See our guide on editing the hosts file for detailed information on how to do this.
Summary
With these techniques it may be possible to find the real IP address of a website that would otherwise be hidden behind Cloudflare. Of course these methods are not a silver bullet and will therefore not always work, however in general I have found them quite useful in identifying the actual server address. Now that you are aware of these methods you could secure your website in order to protect it further with the mitigations discussed to help avoid leaking the IP address of your web server.
Once the real IP address of the web server is known, any protection that Cloudflare offers is lost. The web application firewall is skipped entirely along with any HTTPS rewrites or DDoS protection.
very nice information
No need for any specific tools, you can just use cURL
What are you going to curl? Curling the target domain will give you the Cloudflare IP, not the back end server IP.
This is still complicated for me.
Which part don’t you understand?
You could also try https://cloudsearch.cf. same principal but it’s free and includes an API
Curl the IP address and add a host header, like so:
curl -H 'Host: domain.com' https://1.2.3.4/
No need to muck with host file entries et al. If you want to have a bit more fun, use openssl s_client.
cool
Does this really work????
I do Not think so.
I’ve used the concepts in this article plenty of times during penetration tests.