BitLocker and Secure Boot are important features for a secured Windows operating system to defend against boot and offline attacks. This post will show you how to enable BitLocker to use secure boot for platform and BCD integrity validation.
During the boot process BitLocker will check that the security sensitive boot configuration data (BCD) settings have not been changed since BitLocker was enabled, recovered, or resumed.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
BitLocker and Secure Boot
A computer with UEFI firmware is able to use Secure Boot to provide advanced boot security. Secure Boot restricts the system so that it may only execute signed binaries from a specific authority, preventing the execution of unknown code.
When BitLocker uses Secure Boot for platform and BCD integrity validation it will ensure that the computers pre-boot environment only loads firmware that is signed by authorized publishers. Secure Boot will also provide more flexibility for managing pre-boot configuration compared to the legacy BitLocker integrity checks.
The BCD is stored on the 500MB System Reserved partition, the Windows boot manager reads this during boot.
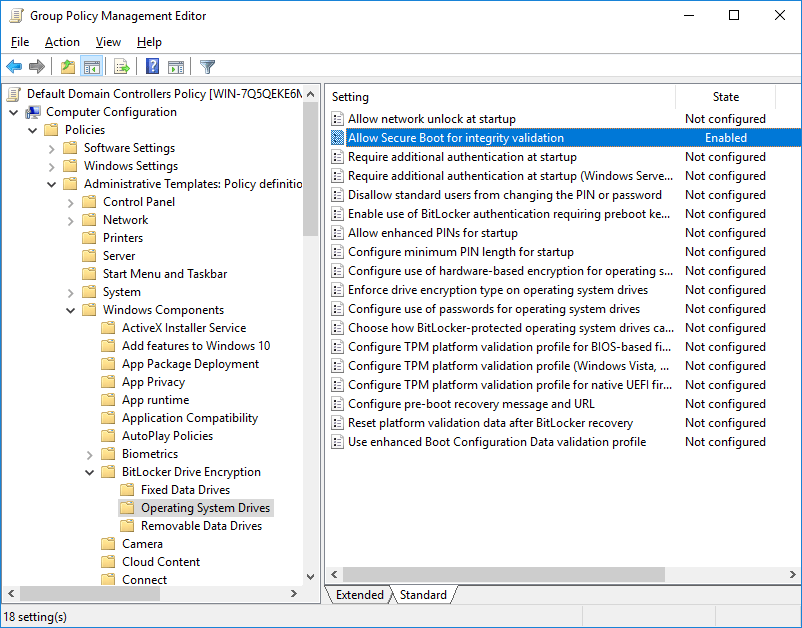
To enable Secure Boot for platform and BCD integrity validation, we must either allow or not configure the “Allow Secure Boot for integrity validation” group policy item, which can be found in Computer Configuration > Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives.
Setting it explicitly to enabled, or otherwise not configuring it at all (this is the default), BitLocker will use Secure Boot for platform integrity if the platform is capable of Secure Boot based integrity validation. Secure Boot ensures that the computers pre-boot environment will only load firmware that has been digitally signed by authorized publishers.
Alternatively if you disable this policy setting, BitLocker will use legacy platform integrity validation, even on systems capable of Secure Boot-based integrity validation.
A benefit of using Secure Boot is that it can fix BCD settings during system boot without needing to trigger a recovery event. Secure Boot enforces the same BCD settings as BitLocker. Secure Boot BCD enforcement is not configurable from within the operating system.
In Windows 7 / Server 2008 R2, BitLocker validated almost all BCD settings that have the winload, winresume, or memtest prefixes. This high level of integrity validation caused BitLocker to go into recovery mode for benign setting changes, which to be honest is just annoying as you’d have to enter the BitLocker recovery key during system boot more often to proceed.
As of Windows 8 / Server 2012 and later however, BitLocker has narrowed the set of BCD settings validated to reduce the chance of benign changes causing a BCD validation problem.
Summary
We have shown you how to use group policy to enable BitLocker to use Secure Boot for platform and BCD integrity validation in Windows Server 2016.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
I have a problem with Secure Boot and Bitlocker. For some reason built-in SYSTEM user is not enought to seal a key to TPM module.
I got error “Bitlocker cannot use Secure Boot for integrity because the UEFI variable ‘SecureBoot’ could not be read”
If I try use domain admin it works fine.
Where is the problem ? This is by designe ?