This post will show you how to enable and configure module, script block, and transcription logging in Windows PowerShell. Module logging allows you to specify the PowerShell modules that you want to log. Script block stores PowerShell commands that are run without the output, while transcription logging records the PowerShell commands that are run along with the full result of the command.
Windows PowerShell 5.0 and above introduce new logging features which we’ll be using here. As we’re using Windows Server 2016 in this example, this is available by default. You can manually download WMF 5.0 to install in Windows Server 2008 R2 or Windows 7 SP1 and above which will give you PowerShell 5.0 if you need it in an older operating system.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Configure Module, Script Block, and Transcription PowerShell Logging
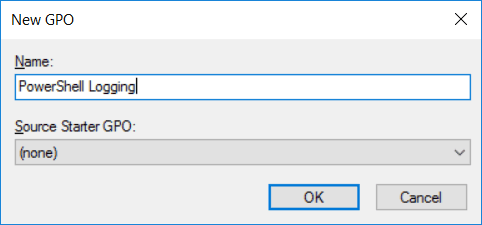
To begin open up Group Policy Management, this can be done either through Server Manager > Tools > Group Policy Management, or by running ‘gpmc.msc’ in PowerShell or Command Prompt. At this point you can either create a new policy, or edit an existing policy. In this example we’ll create a new GPO called “PowerShell Logging”.
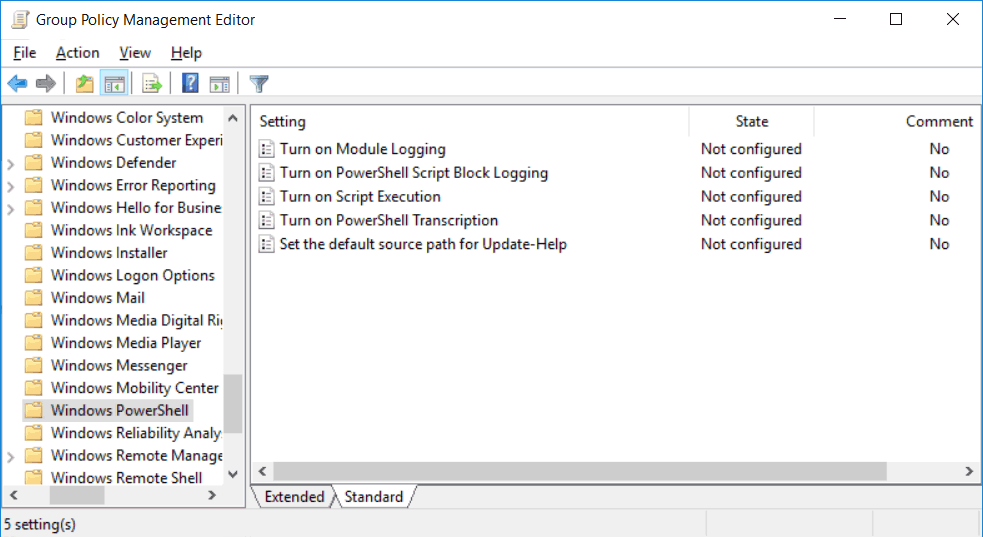
Edit the policy, and browse to Computer Configuration > Policies > Administrative Templates > Windows Components > Windows PowerShell. From within here, either double click or right click then select properties on the policy that you wish to edit. There are a few different policies here that we’ll now discuss.
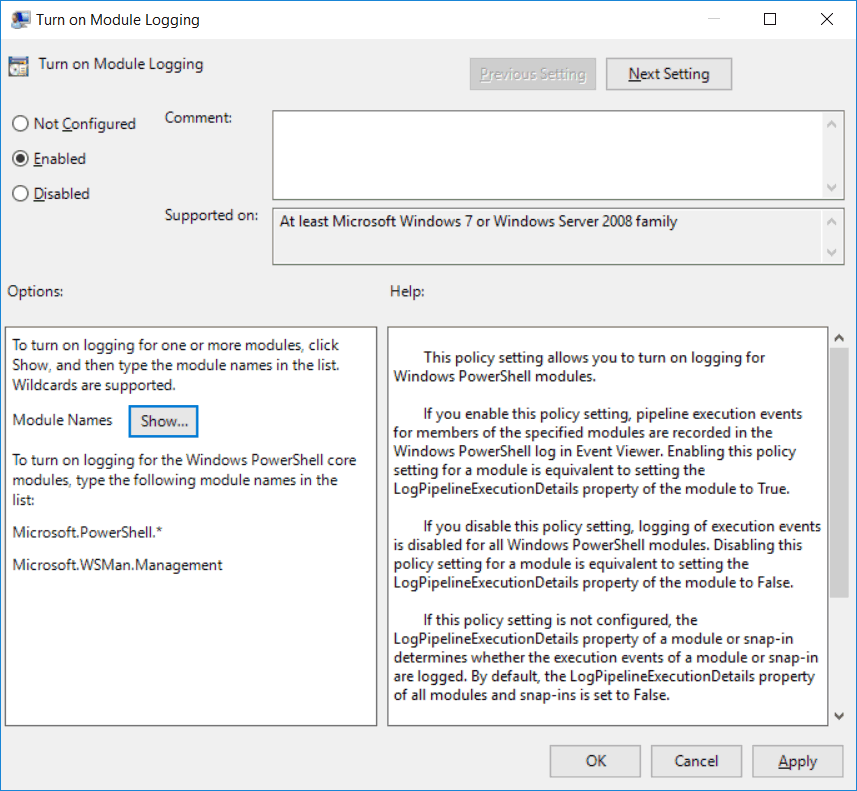
Turn on Module Logging
This policy will allow us to log PowerShell cmdlets that come from a specific module that we specify. By enabling this policy setting, pipeline execution events will be stored in the Windows PowerShell log in event viewer.
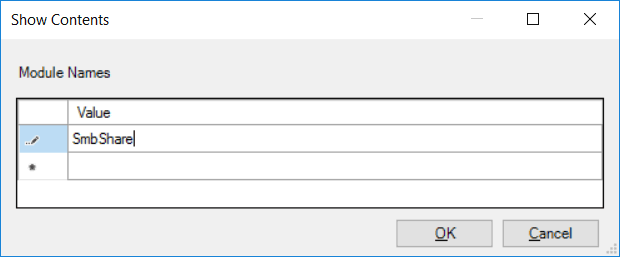
To specify the PowerShell modules that we want to enable logging for we click the “Show…” button, which opens up the interface below. From this window we simply specify the name of the PowerShell module or modules that we wish to log for. In this example we want to log any PowerShell cmdlet provided by the SmbShare module that is run.
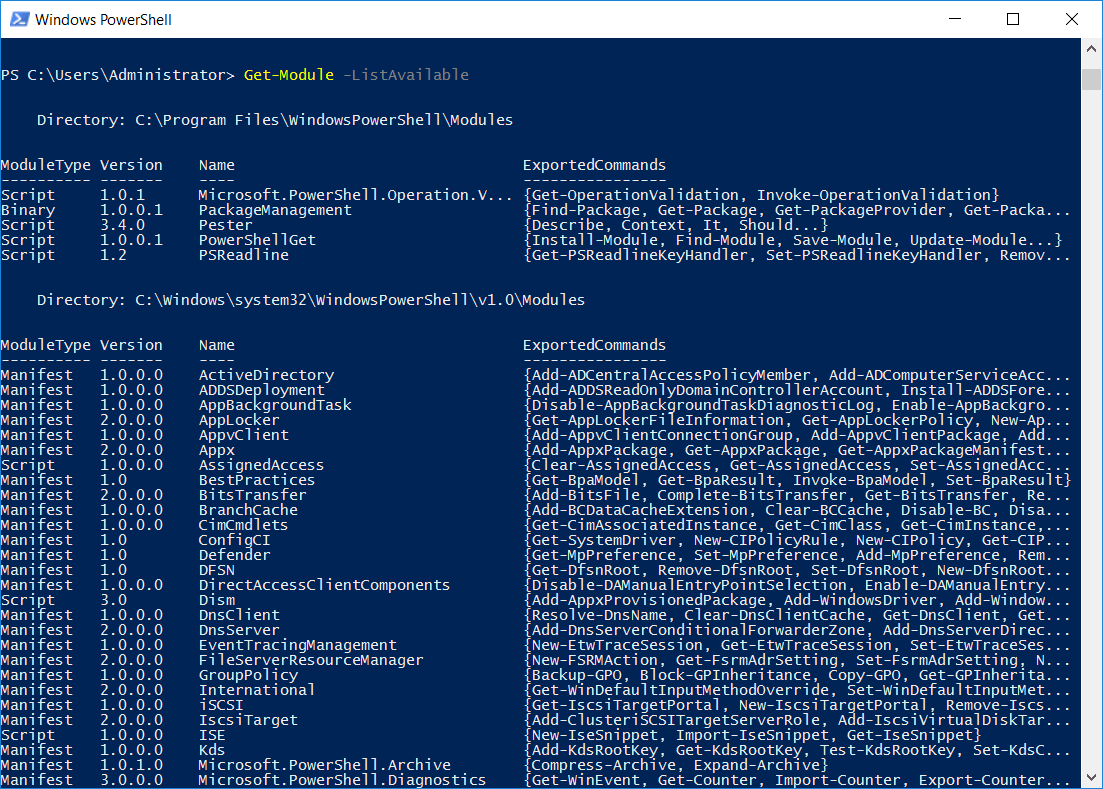
If you are not sure of the module name that you need, you can run the ‘Get-Module -ListAvailable’ PowerShell cmdlet, which will print out a list of all available module names. Under the ExportedCommands column we can see the cmdlets that are included as part of the module. You can pipe the output into ‘Format-List’ to view all of it.
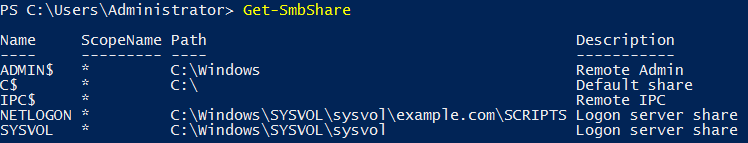
We simply apply this policy to the site, domain, or organizational unit (OU) and then perform a system reboot as this is a computer policy and will not otherwise apply. Once booted up, we then run a PowerShell cmdlet from the SmbShare module. We’ll use Get-SmbShare in this example.
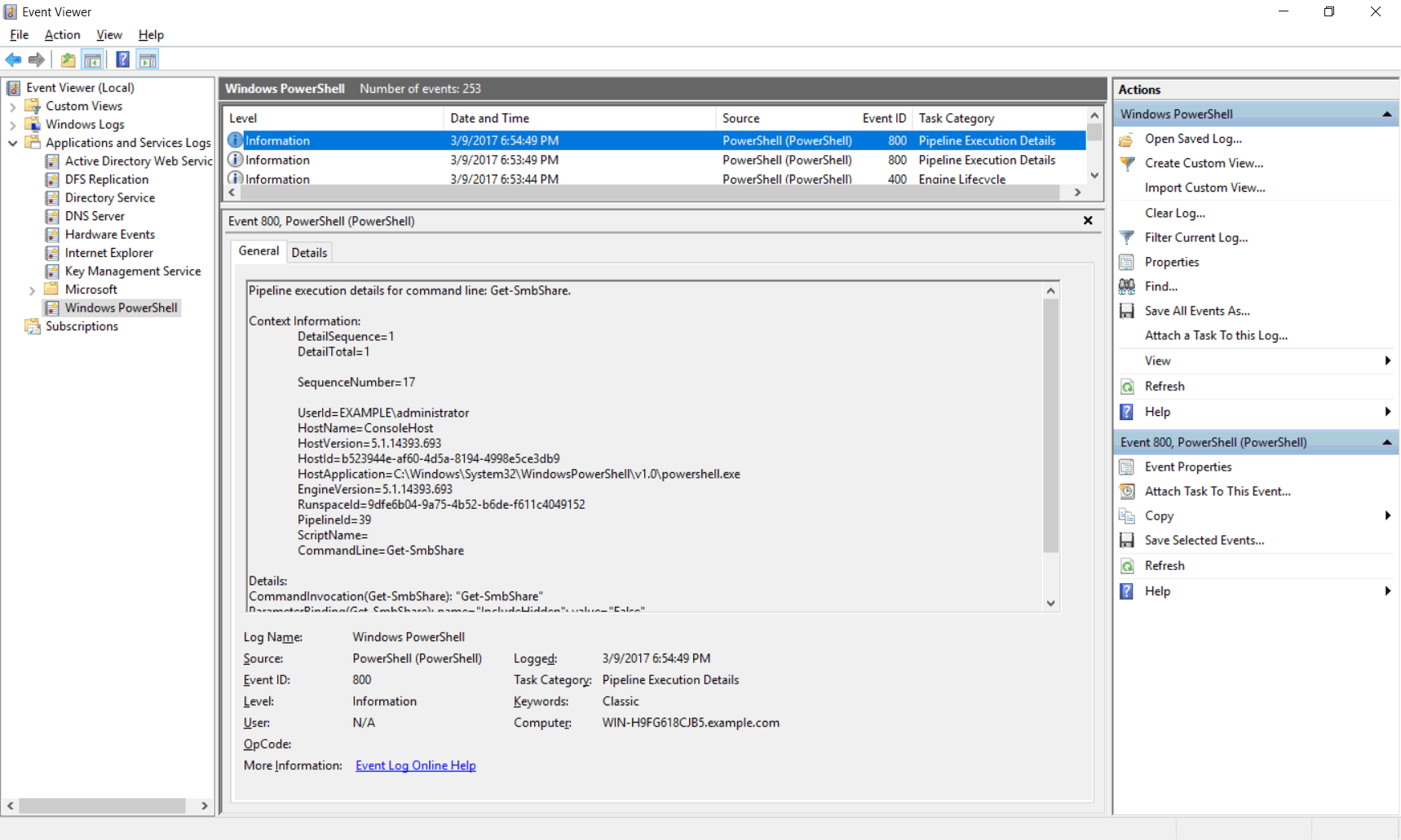
Now if we view Applications and Services Logs > Windows PowerShell in event viewer we should see that this cmdlet is logged. Note that the output is not logged, we’ll cover this later.
PowerShell cmdlets from modules other than SmbShare will not be logged in this manner. To test this I ran some others such as ‘Get-WindowsFeature’ however it did not display in the log.
Turn on PowerShell Script Block Logging
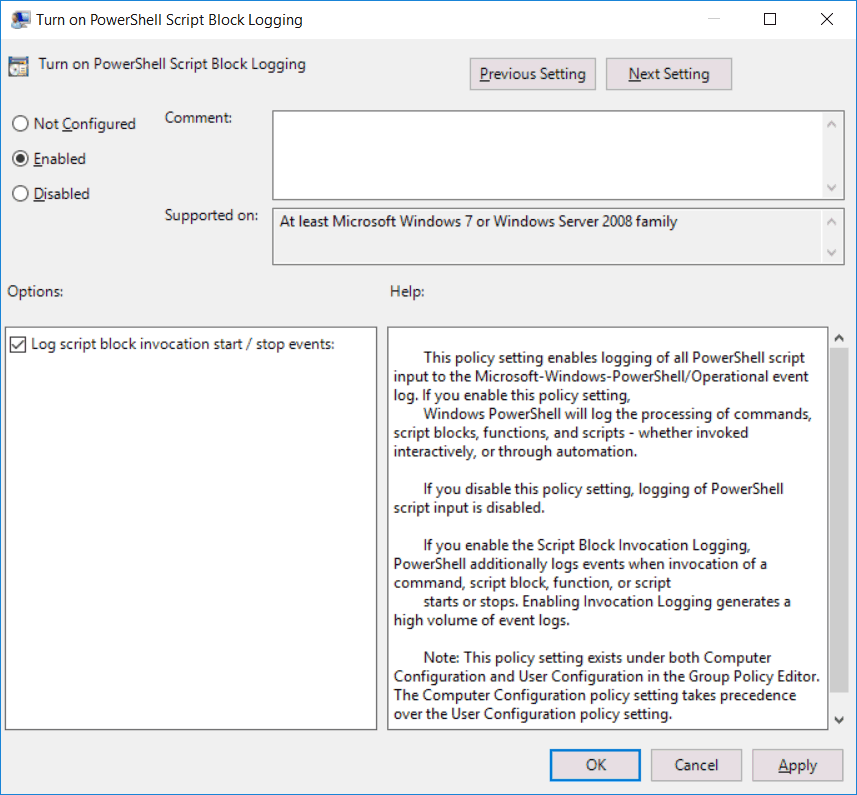
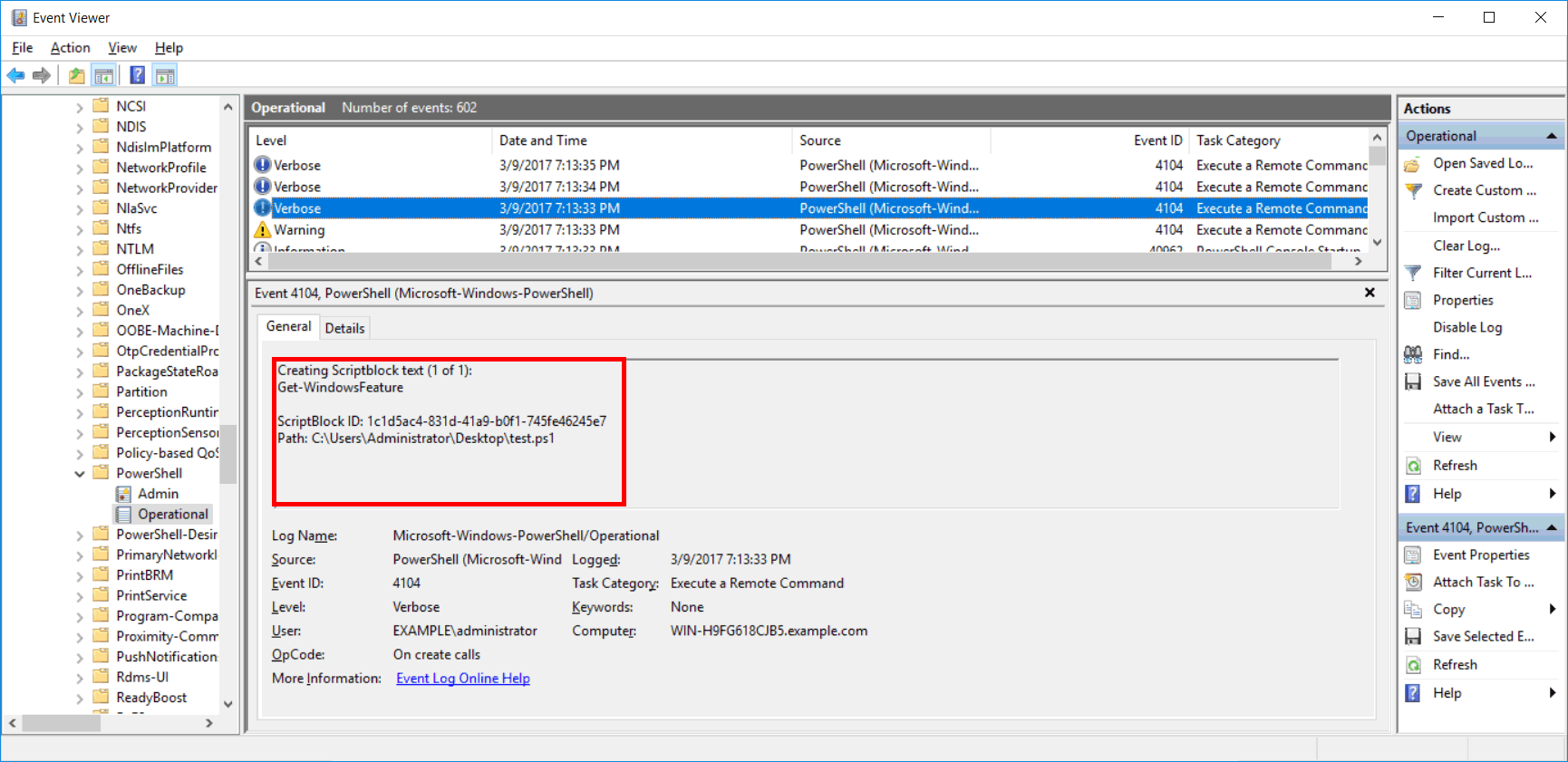
Enabling the script block logging PowerShell policy will store all PowerShell script input into the Microsoft-Windows-PowerShell/Operational event log. This will log various code blocks as PowerShell runs them including commands and scripts. This policy also does not log the output of the PowerShell that was run.
We can optionally select the check box to also log script block invocation start / stop events, which we have done here. Note that this may generate a large number of logs.
I’ve now created test.ps1 on the desktop which simply runs ‘Get-WindowsFeature’. After running this script and checking the Application and Services Logs > Microsoft > Windows > PowerShell > Operational event log, we can see that this activity was logged.
Turn on PowerShell Transcription
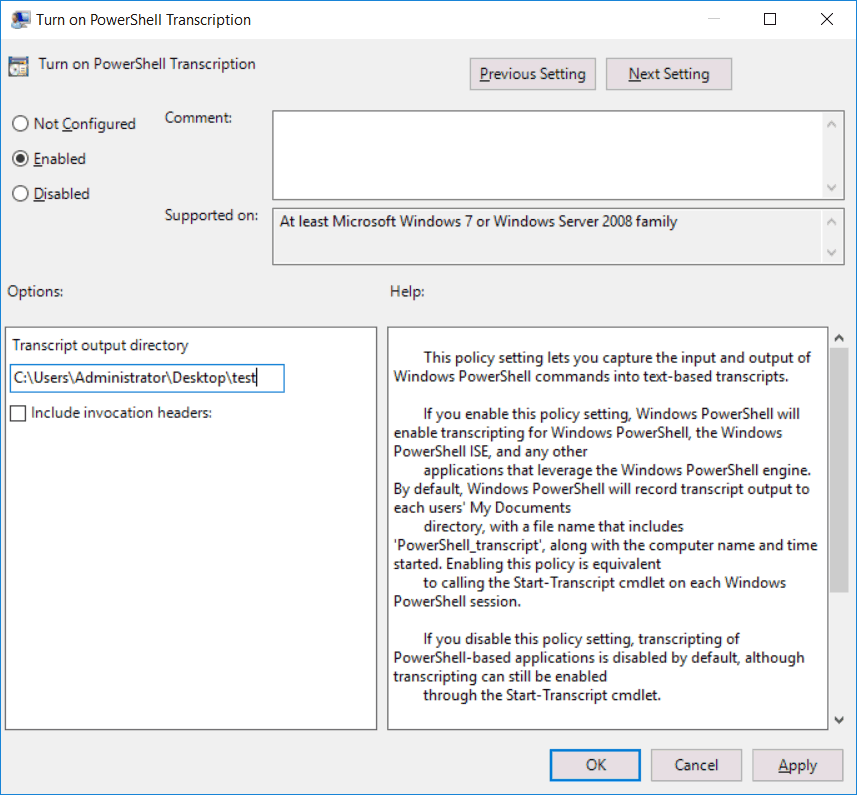
Enabling this policy will log both input and the resulting output of PowerShell into a text file. We need to specify a folder to store the logs to, in this example I’ve selected the test folder on the administrator users desktop.
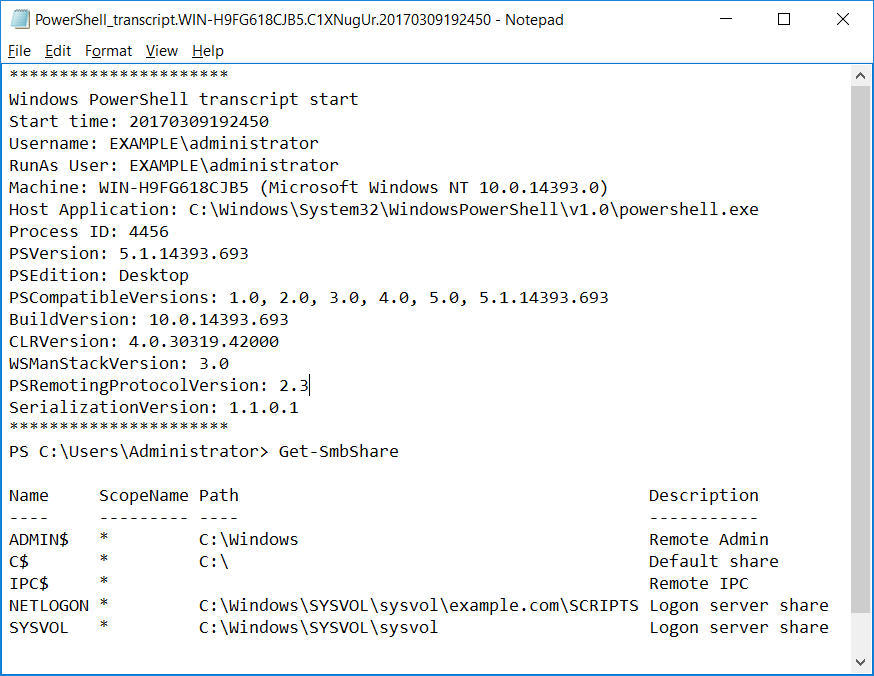
After enabling the policy and running ‘Get-SmbShare’ in PowerShell we can view the folder specified. There’s a PowerShell transcript text file which we can open to view the logs. We can see the PowerShell cmdlet that was run as well as the output have been logged.
There’s also plenty of other useful information here, such as the version of PowerShell in use, the user that ran it, when it was run, the machine it was run on, and the process ID just to name a few examples.
Summary
We have shown you how to use group policy to enable and configure module, script block, and transcription logging in Windows PowerShell. These different policies allow us to log different components of PowerShell which is made possible thanks to the new features available in PowerShell 5.0 and above.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
I am using server 2016 but still couldnot other options than “Turn on Script Execution”
nice thank you;i;m always trying to upload my user id information but blocked it how many times…so maybe having a problem with restriction..love to code