It is certainly ideal to configure BitLocker with TPM if possible, it may be the case that you do not have TPM available but still want to take advantage of BitLocker’s full disk encryption. While this is not possible by default, it is possible after the modification of some group policy settings, which we’ll cover here in order to allow you to deploy BitLocker without a trusted platform module.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Install BitLocker Feature
Before we begin, you will need to install the BitLocker feature in order to proceed. The quickest way to do this is by running the below PowerShell cmdlet which will install the BitLocker feature, note that this will reboot your system to complete the process as per the -Restart parameter on the end.
PS C:\Users\Administrator> Install-WindowsFeature BitLocker -IncludeAllSubFeature -IncludeManagementTools -Restart
Configure Group Policy
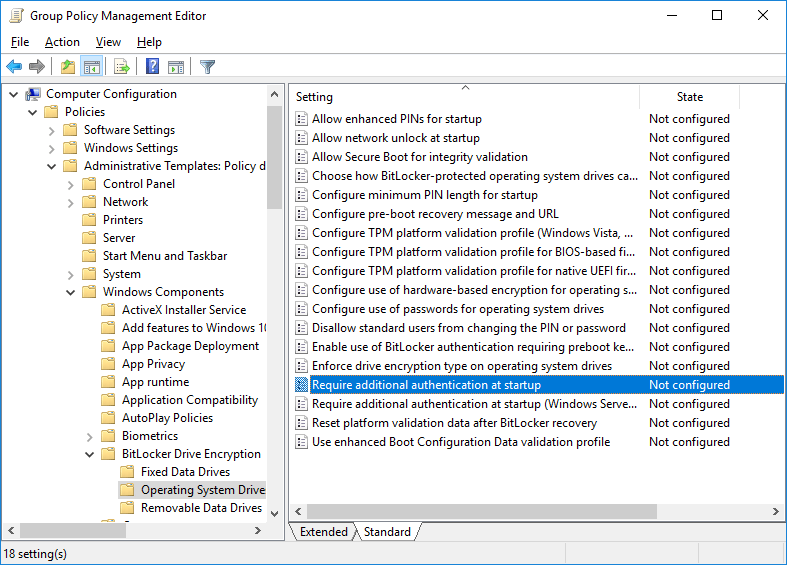
Enabling use of BitLocker without a TPM can be set through the following group policy:
Computer Configuration > Policies > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives > Require additional authentication at startup
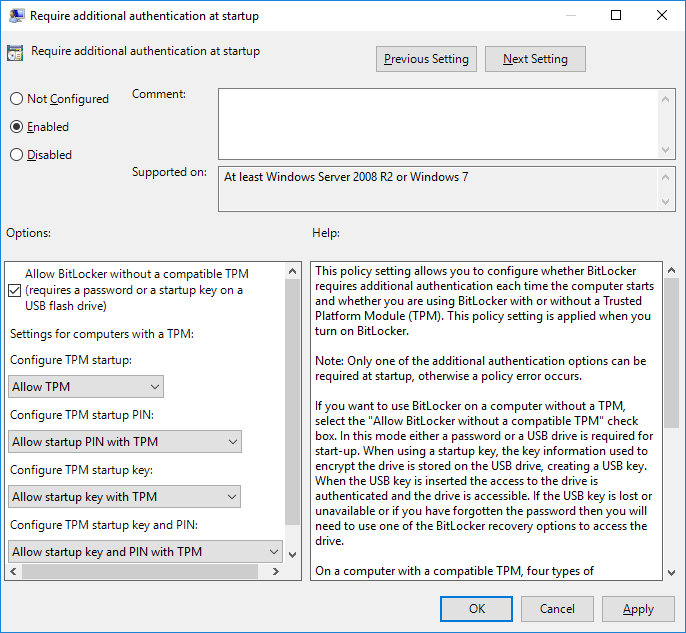
Once this policy is set to enabled, we can select “Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive).
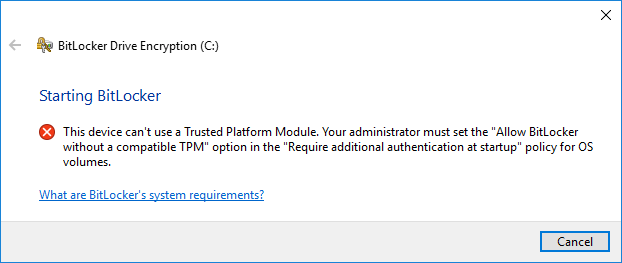
Once the policy changes have rolled out to the computers the policy is linked to, BitLocker can be configured. If this policy is not set and you have no TPM and attempt to enable BitLocker following the steps below, you will receive the below error message telling you to perform the above process first.
Deploy BitLocker without a Trusted Platform Module
Now that the policy has been set to allow us to enable and use BitLocker without TPM we can proceed.
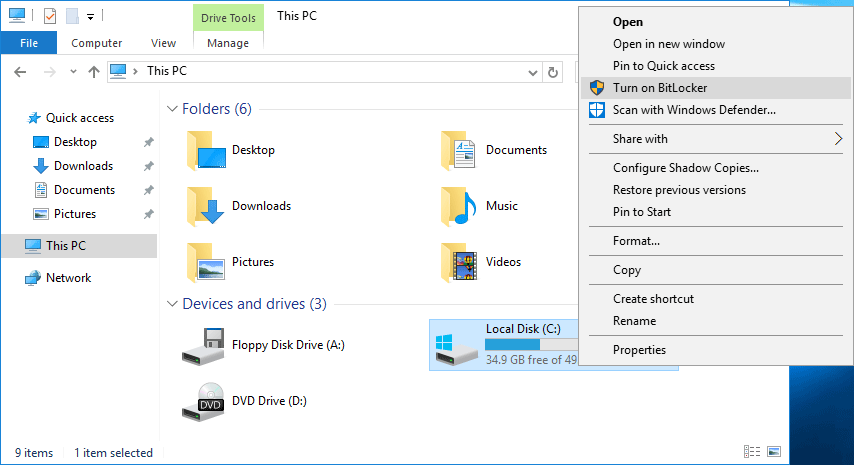
- On the Windows computer that you wish to enable BitLocker, open “This PC” and simply right click the drive that you wish to encrypt and click Turn on BitLocker. In this example we’re using the operating systems primary boot drive.
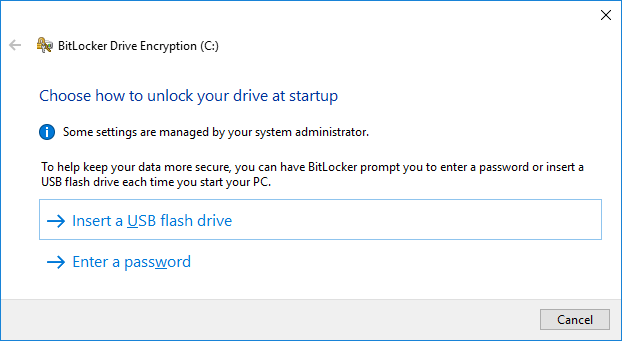
- The BitLocker Drive Encryption wizard will now open. Select if you’re using a USB flash drive or password. At least one of these options must be used, as we are not using a TPM.
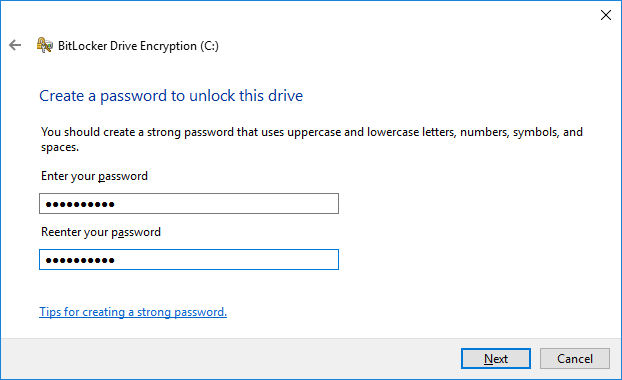
- In this example we will use the password method, be sure to set a strong password.
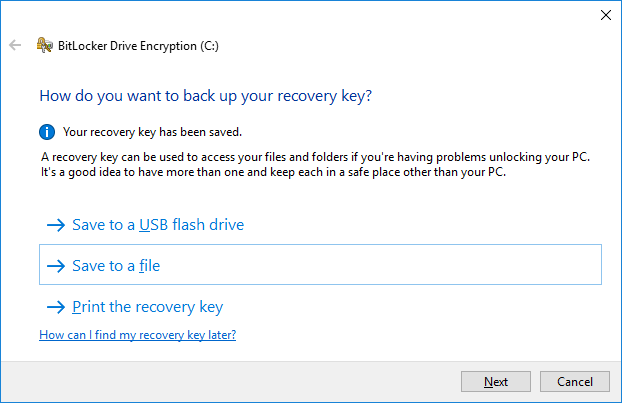
- Next you need to save the recovery key. This can either be done by saving it to a USB flash drive (not the same one that you would use for the startup key), to a file (this cannot be on the same drive that is about to be encrypted), or you can optionally print it. Keep the recovery key safe, if you forget or lose the BitLocker password the recovery key is the only way that you’ll be able to read the encrypted data. Without either you will lose all access, recovery is impossible.
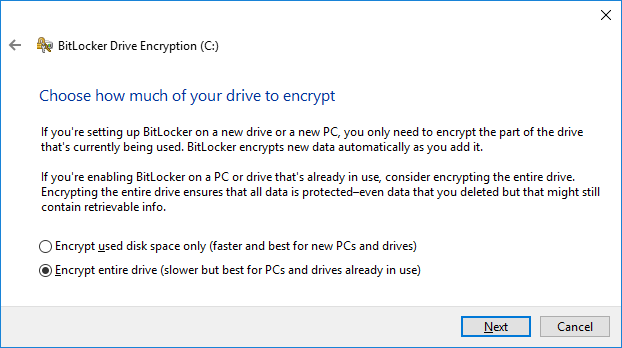
- Now you can select how much of the drive you want to encrypt. You can either encrypt only the space that is actually used, or encrypt the full disk straight up. Personally I always choose to just do the whole thing from the get go.
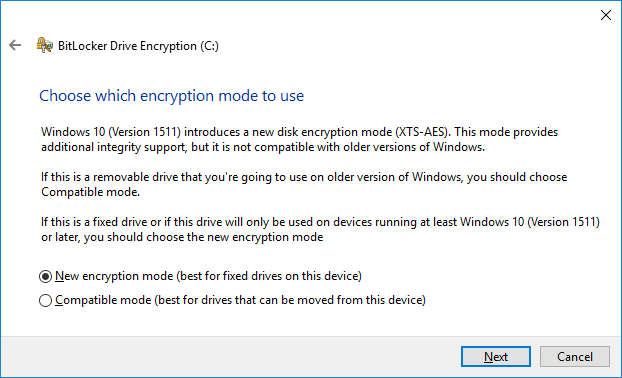
- Choose the encryption mode to use, basically if you’re going to be accessing the disk with versions of Windows older than 10 you will need to select the compatible mode.
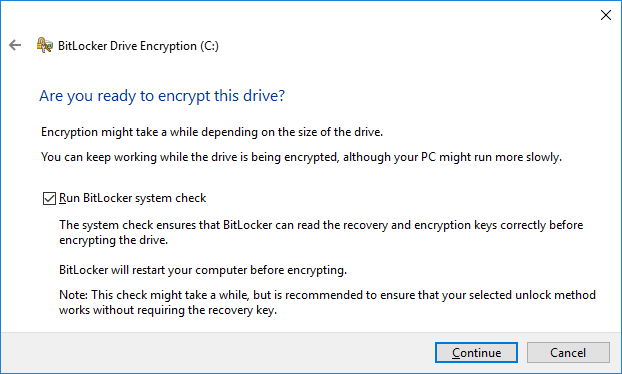
- Finally select continue in order to encrypt the drive. Leave the run BitLocker system check box selected to ensure that there will be no problems prior to encrypting the drive. If problems are detected, encryption will not begin.
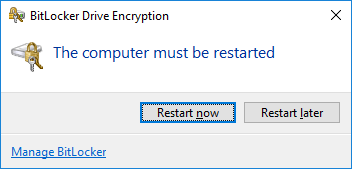
You will now be prompted to perform the reboot to start the BitLocker system check.
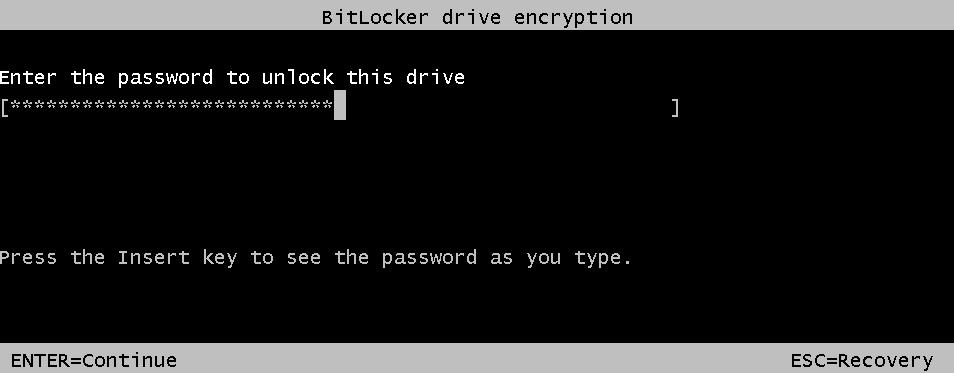
- Assuming everything runs smoothly, you will be prompted for the BitLocker password on system boot.
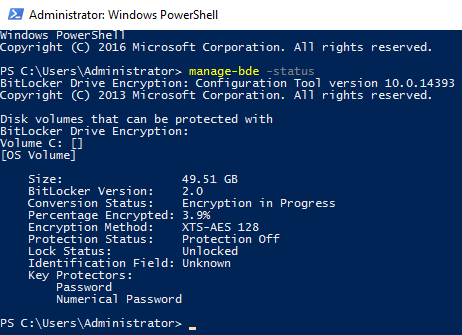
- After you log back in you’ll be able to view the status of the BitLocker encryption assuming the check was successful. This can be done by running ‘manage-bde -status’ in PowerShell. The “Key Protectors” list password only as this is what we are using. If TPM was in use, it would be listed here too.
That’s it, the disk will continue encrypting in the background, BitLocker has successfully been setup without a TPM.
Summary
After configuring the appropriate group policy setting we were able to deploy BitLocker without a trusted platform module available.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Using Bitlocker without TPM would be hipaa compliant or not??
Sorry, I don’t know anything about security compliance like HIPAA so I can’t comment.
Your description and steps have been fantastic! Thank you!
No problem at all, cheers!