We can configure Windows Defender scans using Windows PowerShell as an alternative to configuring them through the graphical user interface. This allows us to integrate Windows Defender features into PowerShell scripts, and configure settings that are not available through the graphical user interface.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Configure Windows Defender scans using Windows PowerShell
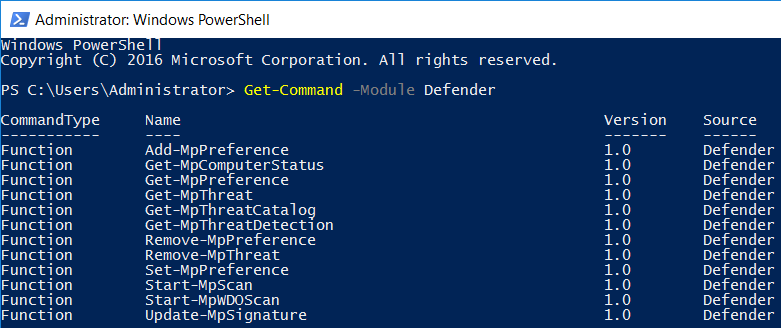
Let’s take a look at the various PowerShell cmdlets for Windows Defender that are available to us in Windows Server 2016. We can view all cmdlets provided as part of the Defender module as shown below.
Next let’s find out what each of these actually do.
- Add-MpPreference: This cmdlet is used to modify settings for Windows Defender.
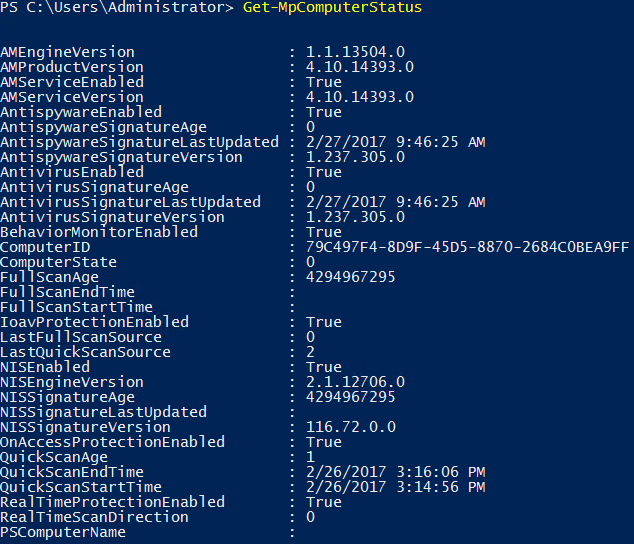
- Get-MpComputerStatus: This cmdlet can be run to retrieve the status of Windows Defender.
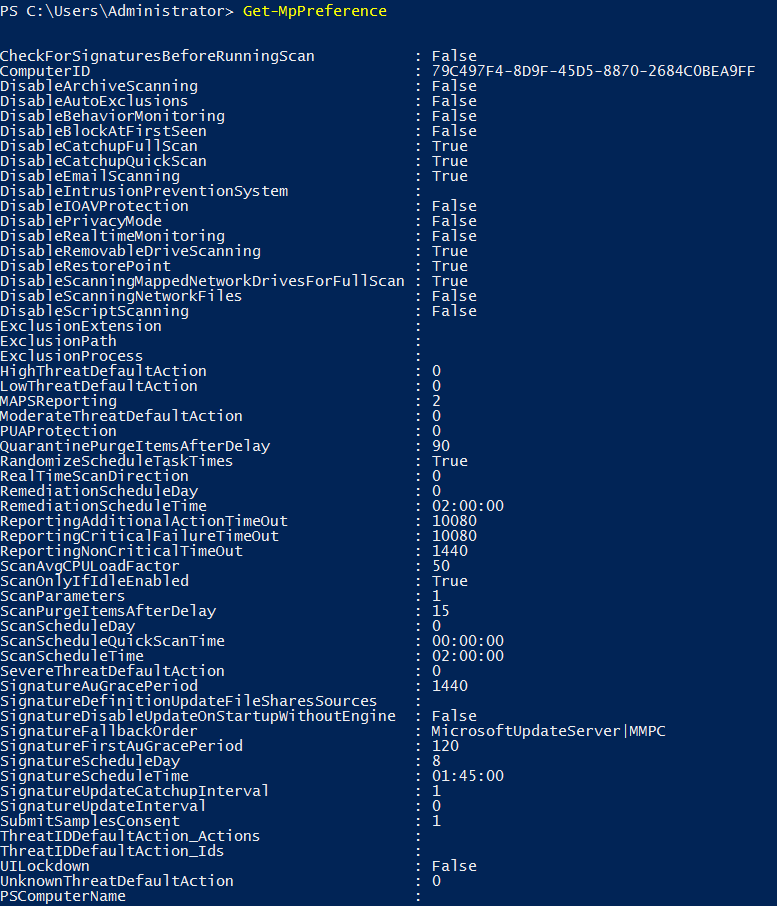
- Get-MpPreference: This cmdlet gets the preferences for Windows Defender scans and updates. Running it will output a list of detailed settings, most of which can only be modified through PowerShell or via group policy.
- Get-MpThreat: This cmdlet will display the history of detected threats from previous scans.
- Get-MpThreatCatalog: This cmdlet displays known threats from the definitions catalog which contains information about all known threats that Windows Defender can detect – This cmdlet displays a lot of information.
- Get-MpThreatDetection: This cmdlet will display current and prior threats that have been detected by Windows Defender.
- Remove-MpPreference: This cmdlet is used for removing custom items that have been added, such as exclusions or default actions.
- Remove-MpThreat: This cmdlet will remove all threats that have been detected from Windows Defender.
- Set-MpPreference This cmdlet is used for configuring specific settings that were displayed from the Get-MpPreference cmdlet.
- Start-MpScan This cmdlet starts a typical Windows Defender scan of the system.
- Start-MpWDOScan: This cmdlet starts a Windows Defender offline scan. An offline scan will reboot the system into a trusted environment and perform a scan without booting into your normal operating system.
- Update-MpSignature: This cmdlet will update the antimalware definitions.
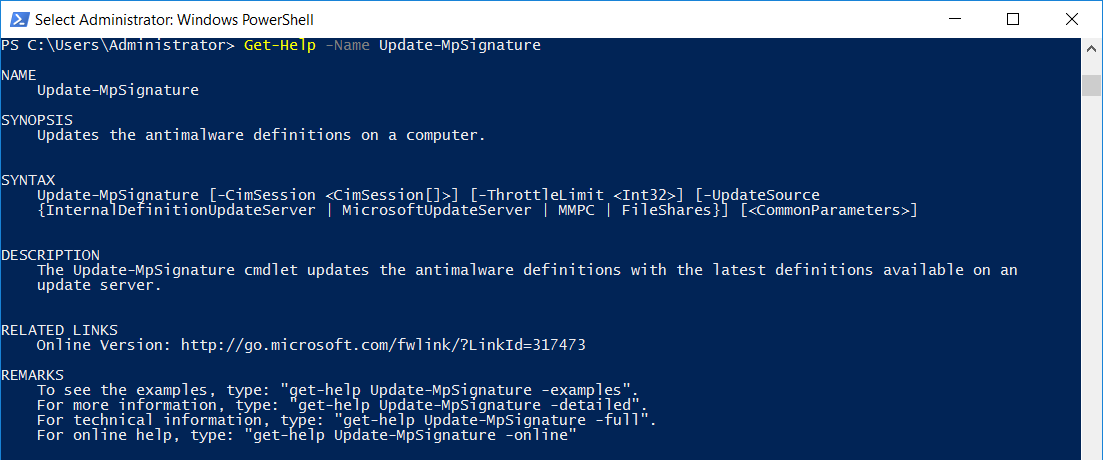
We can view the built in documentation for any of these cmdlets in PowerShell itself with ‘Get-Help’, as shown here. We first run ‘Update-Help’ to ensure that our help files are fully up to date, if we don’t run these we may be asked when running ‘Get-Help’ anyway.
PS C:\Users\Administrator> Update-Help PS C:\Users\Administrator> Get-Help -Name Update-MpSignature
We can also use -Examples, -Detailed or -Full with Get-Help to view even more information if needed.
We can see that this has given us an explanation with regards to what the specified cmdlet does, syntax information for using it, and even a reference to the command online with further information.
Summary
We’ve now shown you how to configure Windows Defender scans using Windows PowerShell. We can perform updates, initiate scans, view history, and customize specific settings that are not available through the graphical user interface thanks to PowerShell.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
0 Comments.