By default the Encrypting File System (EFS) uses self signed certificates that are tied to a user account. Should these be lost a user will no longer be able to access their encrypted files. We can configure the EFS recovery agent which can decrypt the certificates of other users, thereby providing access to their encrypted files.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Note: We’ll be assuming that you already have Active Directory Certificate Services (AD CS) setup within your domain. This topic will not be covered here, however you can refer to this guide to get setup.
Within a domain environment, the first domain administrator account created within the domain acts as the Data Recovery Agent (DRA) by default. The local administrator fulfills this role on a non-domain joined workgroup machine.
Configure the EFS Recovery Agent
We can set a specific account to be the DRA, we simply need to create an EFS Recovery Agent certificate for it. This means that both the user who encrypted the file will be able to decrypt it, as well as the DRA account. As you can probably guess, it’s critical that the private key for the DRA is protected. It’s suggested that it be securely stored offline when not in use.
In this example we’ll be using group policy to configure a DRA within the entire domain. This DRA will therefore be able to decrypt any encrypted users content with EFS within the domain, very useful in an emergency situation.
To begin open up Group Policy Management, this can be done either through Server Manager > Tools > Group Policy Management, or by running ‘gpmc.msc’ in PowerShell or Command Prompt. At this point you can either create a new policy, or edit an existing policy. In this example we’ll create a new GPO called “DRA”.
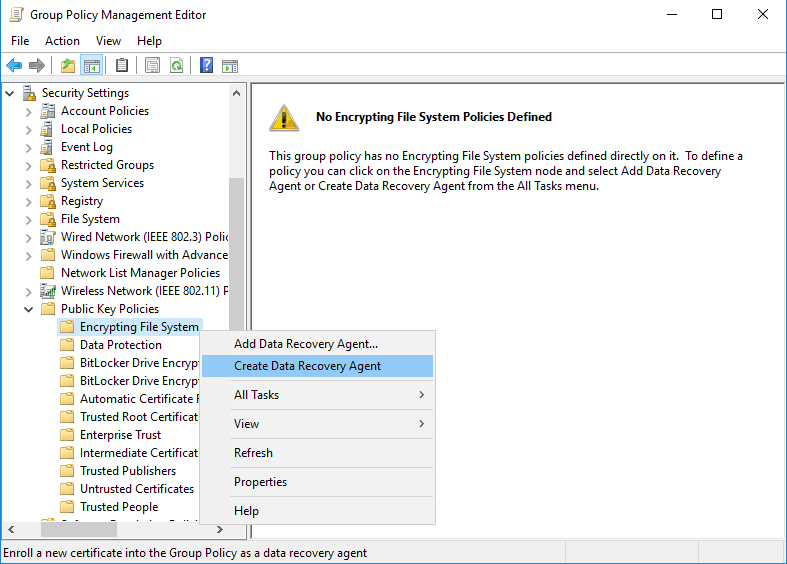
Edit the policy, and browse to Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies > Encrypting File System. Currently we have no EFS policies defined. We can right click the Encrypting File System folder and select Create Data Recovery Agent.
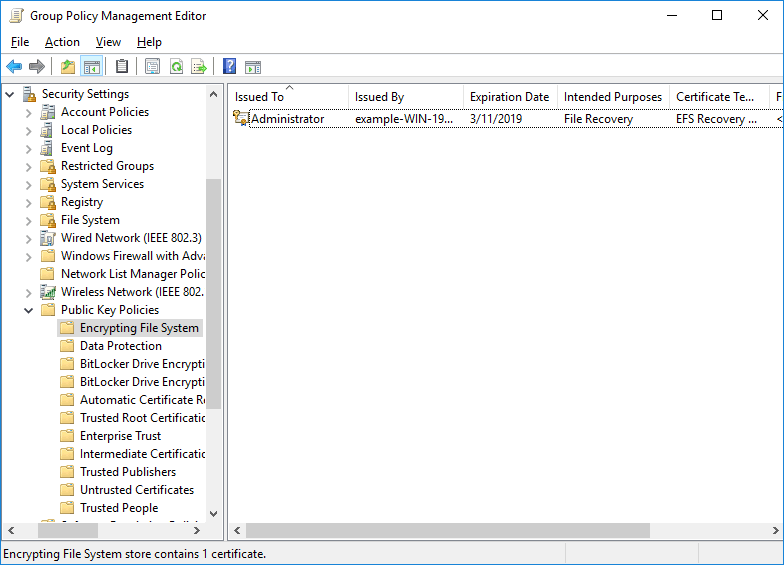
We can see below that this has created a certificate issued by our CA using the EFS recovery agent certificate template. This essentially deploys the administrators certificate to all Windows machines effected by this policy.
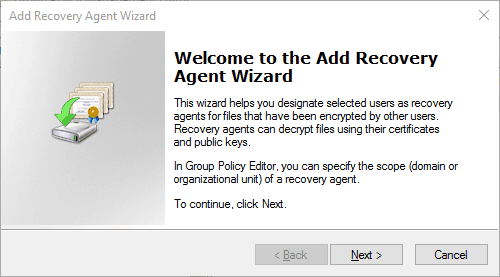
We can also instead right click Encrypting File System group policy folder and select Add Data Recovery Agent, which opens the Add Recovery Agent Wizard.
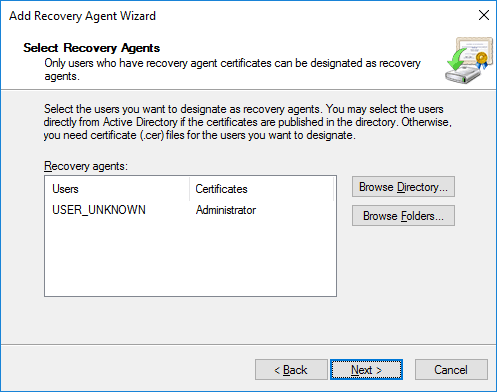
From here we can specify either a user or certificate that can be used as a DRA.
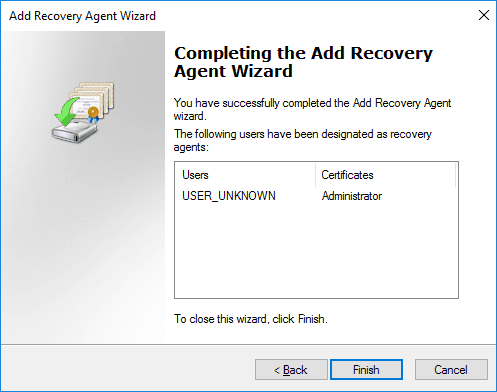
After selecting a user with a certificate published in AD, or a .cer certificate file, we get to the completing the add recovery agent wizard screen where we can view a summary and click finish to complete the process.
We can also use our ADCS PKI to create EFS Recovery Agent certificates for other users as needed, which we’ll cover next. First we’ll cover how to configure the CA, followed by how to configure the client.
Server Configuration
The following configuration takes place on our CA server.
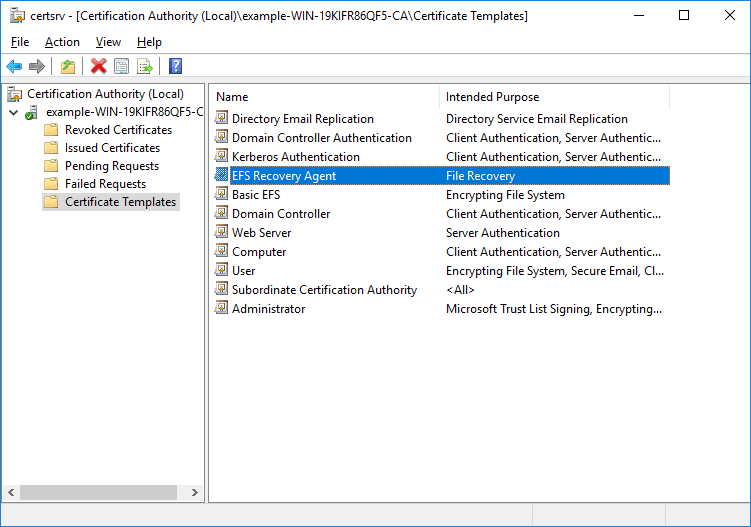
If we go to Server Manager > Tools > Certification Authority, we can see that there is an EFS Recovery Agent Certificate Template that can be used for file recovery.
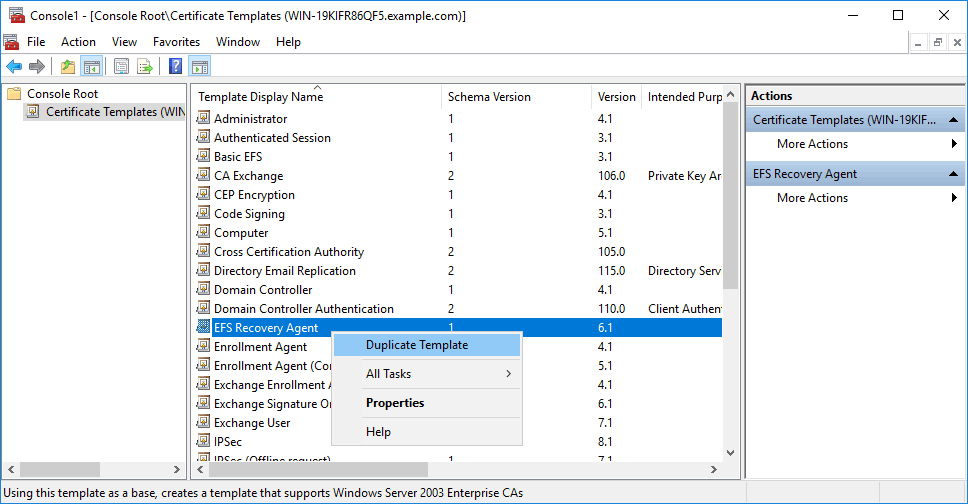
Now we open MMC and select the Certificate Templates snap in. This allows us to right click the certificate template that we want and select duplicate template to create our own custom copy. In this case we want to duplicate the EFS Recovery Agent template. This is the normal process, we don’t typically edit the default templates.
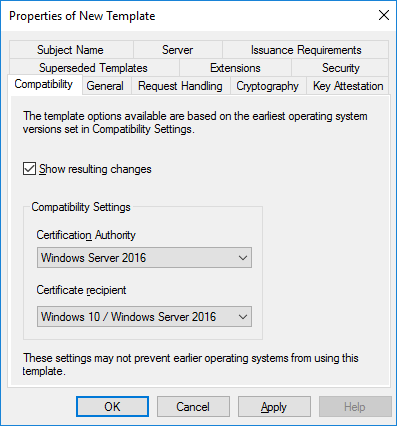
This opens the properties for the new template. All of the settings are copied from the original template that we are copying from, however at this stage we can customize anything we like for our new template.
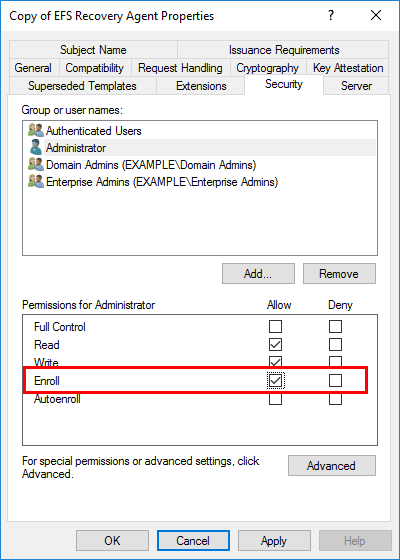
In this case I changed the permissions of the administrator user under the security tab as shown. I set the enroll permission to allow, this allows an administrator to enroll themselves and receive an EFS Recovery Agent certificate.
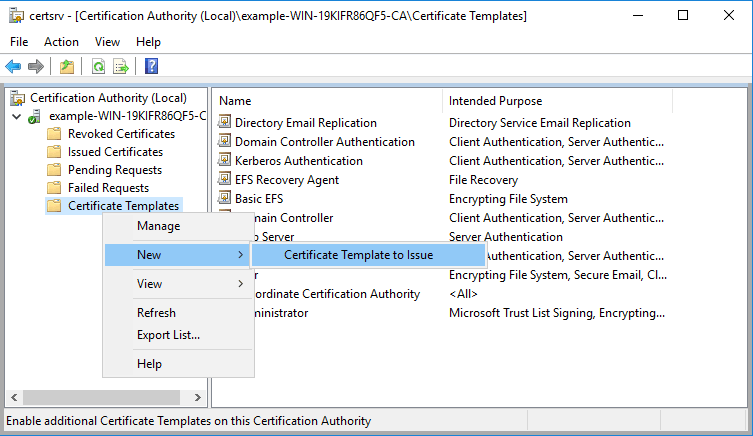
Next in Certificate Authority we right click Certificate Templates, select New, followed by Certificate Template to Issue.
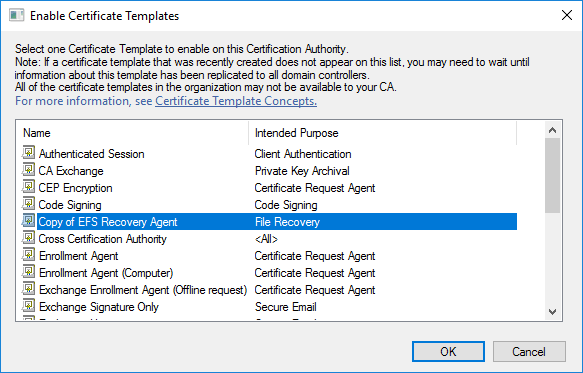
We now select the template that we duplicated, in this example I left the default name which was “Copy of EFS Recovery Agent”, so this has been selected.
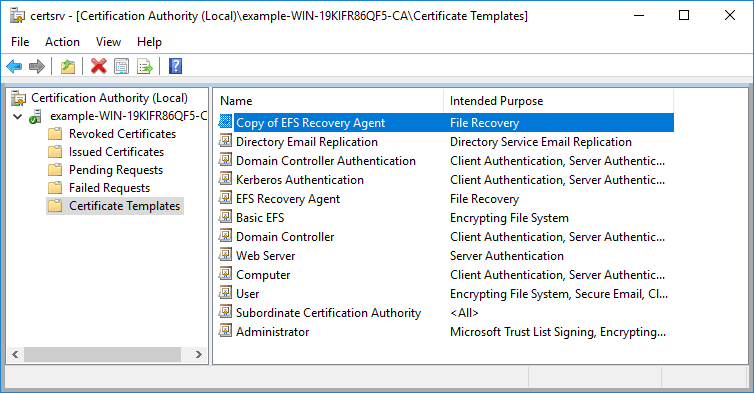
Our duplicated certificate now shows up along with the rest of the certificate templates.
Client Configuration
The following takes place on our client while logged in as a different user.
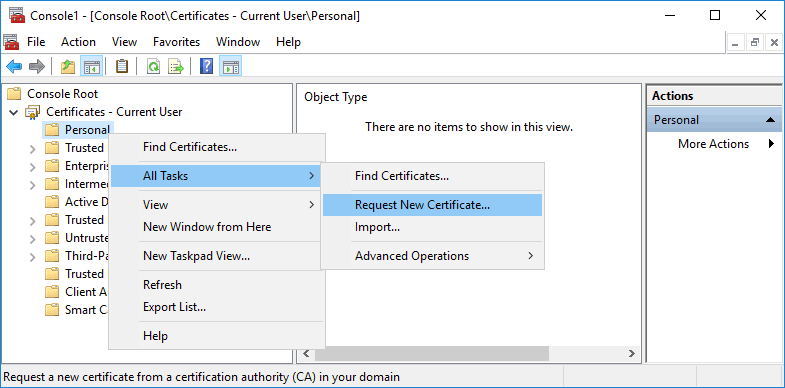
Open the MMC and select the Certificates snap in. Right click Personal and select All Tasks > Request New Certificate.
On the before you begin screen that pops up, click next to continue.
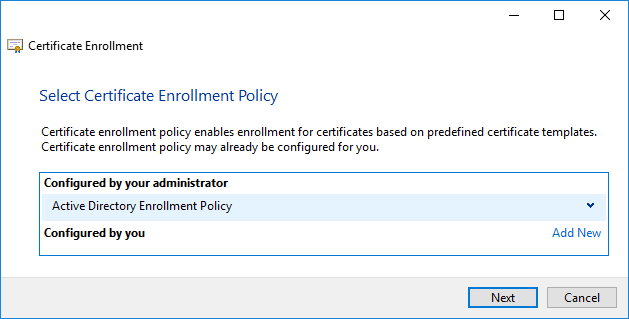
On the Select Certificate Enrollment Policy screen, click next.
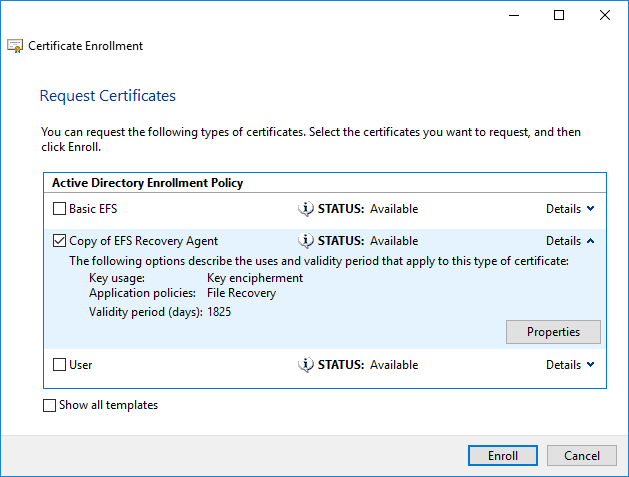
From the Request Certificates screen our duplicated certificate should appear. If this is not the case, confirm that you have set appropriate permissions on the certificate template. The user that you are logged in as must be given the enroll permission. Note that it is probably not a good idea to give the enroll permission to normal users for the EFS recovery agent certificate, as this would potentially allow users to decrypt any encrypted file (assuming it’s deployed via GPO somehow).
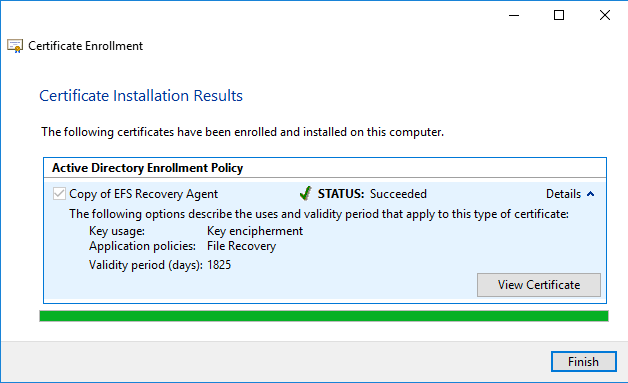
We are now shown the results, we can see that we have successfully enrolled for an EFS Recovery Agent certificate.
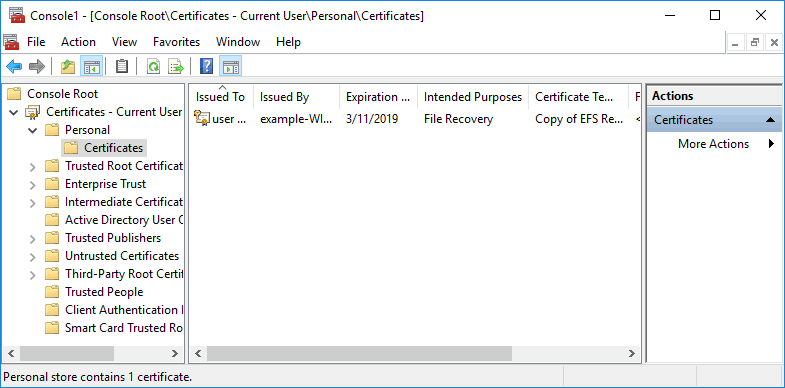
Now if we look under the personal certificate store for this client user, we can see that we do indeed have a file recovery certificate.
If we wanted to get this certificate into the group policy covered previously, we would right click it and select All Tasks > Export. From here we can export the certificate as a .cer file, which can be imported through the Public Key Policies group policy setting as shown earlier. Once the policy has deployed, the new user will be able to use their certificate to read files encrypted with EFS by anyone in the domain going forward.
Summary
We have shown you how to configure the EFS recovery agent within a domain environment using Active Directory Certificate Services. This involves assigning an account to act as a data recovery agent, allowing its private key to recover user data.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
If we wanted to get this certificate into the group policy covered previously, we would right click it and select All Tasks > Export. From here we can export the certificate as a .cer file, which can be imported through the Public Key Policies group policy setting as shown earlier. Once the policy has deployed, the new user will be able to use their certificate to read files encrypted with EFS by anyone in the domain going forward.
>>> nope at all… unluckily. I religiously followed these steps, taking care of updating policies on server/client sides but the new DRA hasn’t access to the files encrypted by another user.